Managed Cybersecurity Solutions
A Custom Security Strategy
With A Multi-Layered Defense
Protect your clients with managed cybersecurity solutions tailored to their unique needs. SOCSoter’s advanced platform provides cloud-based security, real-time monitoring, and compliance solutions. Moreover, our comprehensive MDR+ platform enhances this by combining advanced threat intelligence, real-time response, and compliance support. Backed by 24/7 human-driven SOC monitoring, this customized security stack maximizes protection while reducing workloads, ensuring your clients stay secure and compliant.
Discover scalable solutions tailored to your business needs today!
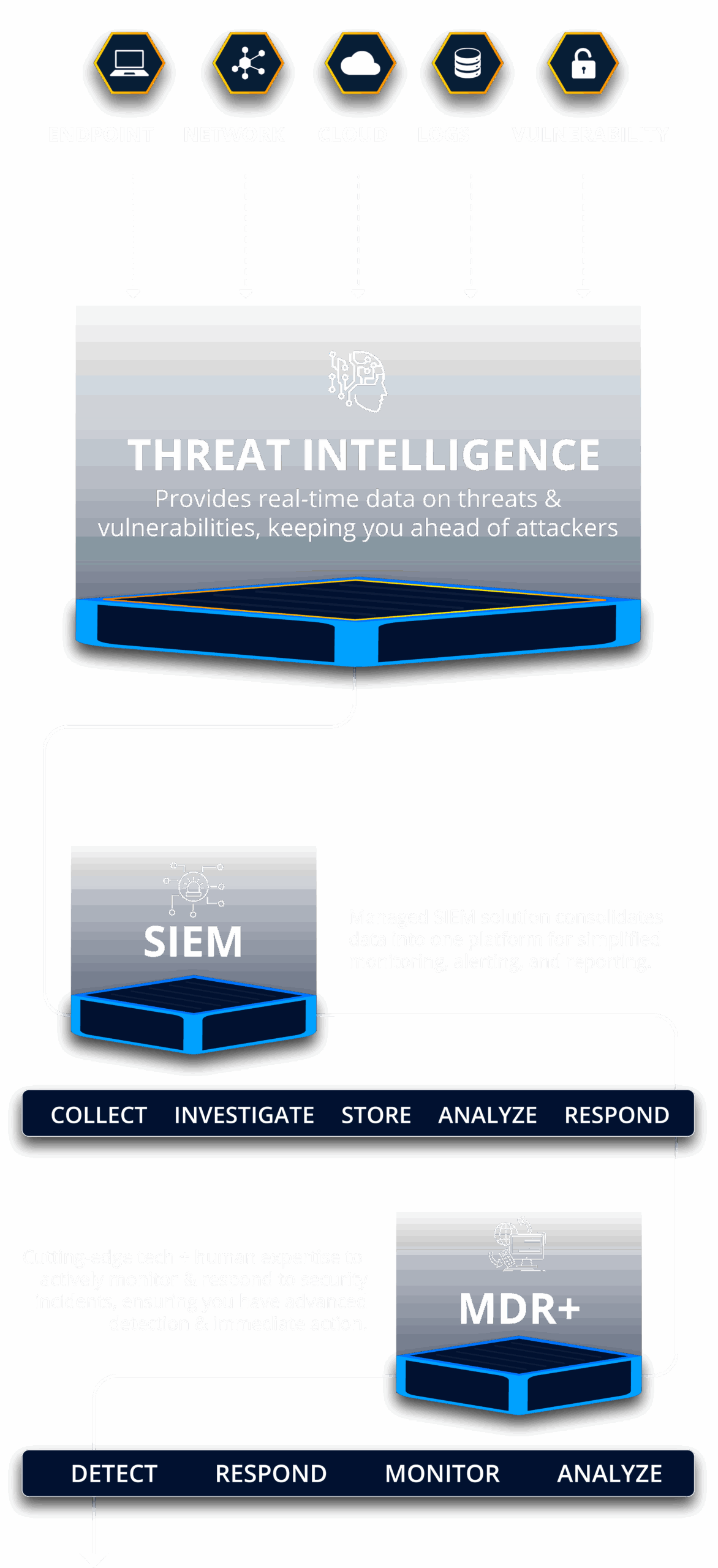
Endpoint | Network | Cloud | Vulnerability | Compliance
DESIGNED FOR YOU. BUILT TO DEFEND.
Comprehensive Managed Cybersecurity
flexible Security for Unique client Needs
We provide a hybrid approach to managed cybersecurity solutions, offering flexibility for individual client needs. Consequently, our managed cybersecurity solutions offer flexibility for individual client needs, integrating features like SaaS application monitoring and cloud security to deliver comprehensive protection. We bridge the gaps left from single solution vendors because we’re more than just a product, service, or stack of tools to manage; in fact, our platform delivers results.

MANAGED SECURITY
24 | 7 US-BASED SOC
24 x 7 x 365 proactive threat detection & rapid response, preventing threats before they occur to minimize damage & reduce client downtime.
Experience Meets Innovation
Not all MDR Platforms are created equal
Centralized Portal
Bring all your security tools into one platform for better analytics, reporting, and visibility.
Customizable Approach
Choose the right package tailored to the specific needs of any organization without long term contracts or predatory terms.
Unlimited Integrations
Streamline integration management and gain complete visibility into vulnerabilities, services, and capabilities within our comprehensive integration hub.
Managed Cybersecurity Solutions Built for You
Your First & Last Line of Defense
The SOCSoter Platform
managed cyberSecurity solutions
This fully managed security platform offers advanced threat protection by combining total endpoint protection, cloud application monitoring, and network monitoring SIEM. Moreover, with 24/7/365 Managed SOC services, our expert security analysts provide comprehensive threat detection and rapid response that you can count on.
Your Factor to Complete
Managed cybersecurity
By collecting and analyzing data from multiple sources, we detect and respond to advanced threats and identify complex attacks, which allows us to see the bigger picture.
As a result, this ensures that we provide a complete picture of potential threats to our clients’ systems that may go unnoticed when relying on a single data source or tool for visibility.
Ultimate All-In-One
comprehensive MDR+ Solution
We understand the challenges organizations face when thinking about hiring, training, and retaining skilled cybersecurity professionals. Furthermore, the number of tools needed to maintain good cyber hygiene in a business is a growing concern.
In response, built from the ground up to tackle these challenges with proven technology, SOCSoter is the most comprehensive partner solution in the managed cybersecurity industry.

Threat Intelligence PLATFORM
CENTRALIZED LOG COLLECTION
By gathering logs from various network sources, we provide a single, clear view of all security events, thereby making it easier to identify and investigate anomalies.
REAL TIME ALERTS & NOTIFICATIONS
This ensures timely identification of suspicious activities by triggering automated alerts based on predefined rules, therefore helping you respond to threats in real-time.
COMPLIANCE REPORTING
The system provides detailed audit trails and reports, which help your organization meet regulatory compliance requirements effortlessly, including HIPAA, GDPR, and CMMC.
SECURITY INFO & EVENT MANAGEMENT
REAL TIME THREAT IDENTIFICATION
Constantly monitors global cyber activities in order to identify new and emerging threats, therefore ensuring your organization is never blindsided by the latest attack trends.
ADVANCED DATA CORRELATION
It combines threat data from multiple sources, thereby giving you a comprehensive view of possible attack vectors and providing actionable recommendations for immediate response.
AUTOMATED THREAT ANALYSIS
Using machine learning to automatically categorize and analyze threats, thereby reducing manual investigation time and allowing quicker mitigation of high-priority incidents.
MANAGED DETECTION & RESPONSE +
24/7 THREAT MONITORING
It ensures continuous monitoring of your network, systems, and endpoints, so that no suspicious activity goes unnoticed, even during off-hours.
INCIDENT RESPONSE
Immediate expert response to detected threats, thereby minimizing the damage and downtime by containing and eliminating malicious activities quickly.
BEHAVIORAL ANALYTICS
It utilizes advanced machine learning to track unusual behavior across users and systems, thus allowing early detection of insider threats or sophisticated attacks.
SOCSoter Supported Compliance Frameworks








Why SOCSoter?
A robust defense that combines advanced technology with the expertise of cybersecurity professionals. In addition, we don’t just monitor your systems— our managed cybersecurity solutions actively detect, analyze, and react to threats in real-time, ensuring your business stays protected against the latest cyber challenges.
Advanced capabilities
Count on advanced threat detection to identify threats in real time, with deep visibility into your network, proactive threat hunting, & automated response options.
With continuous updates, our platform adapts to evolving threats, keeping your defenses strong & reliable.
customizable Solutions
Managed cybersecurity solutions easily adapt to the changing needs of your organization, whether you’re managing security for a small business or a large enterprise.
Moreover, with flexible options, you can customize your security approach to fit specific requirements, ensuring you always have the right level of protection without unnecessary complexity or cost.
solutions Handcrafted For You
Find The Right One For Your Business
Want to protect an on-premise network or a cloud-native system? You can do both!
Trust the SOC-managed detection and response solutions from SOCSoter.
All solutions include our MDR+ defenses!
SOCSOTER AS YOUR MSSP
Offering a holistic approach with more flexibility and customization compared to a pure-play vendor or MSSP.
Network
monitoring
SIEM technology offers real-time network analysis for threat detection & prevention by providing 24/7 visibility, continuous threat intelligence monitoring, rapid anomaly detection, and tailored solutions for robust defense.
endpoint
protection
Swiftly identifying and containing threats across all connected devices, and with continuous 24/7 SOC management of endpoints to detect vulnerabilities, we efficiently allocate resources. Furthermore, a proactive defense system protects against malware, ransomware, and unauthorized access.
cloud
monitoring
By integrating SaaS apps and third-party monitoring via APIs, we ensure continuous SOC monitoring, threat surveillance, event generation, and alert analysis. Additionally, 24/7 monitoring of cloud data is achieved by merging on-premises and virtual security for effective threat identification.
log collection
analysis & storage
By collecting logs in real-time from various sources, including firewalls, switches, routers, and servers, the service acts as a syslog server, monitoring and analyzing for security threats. Furthermore, the logs are stored off-site for added security, ensuring secure, encrypted storage.
vulnerability
management
Through continuous assessment of outdated software, system misconfigurations, and asset compliance, combined with prioritization, threat intelligence, and real-time insight, we help you understand your exposures. This, in turn, allows you to proactively prioritize remediations.
compliance
services
The SOC SIEM solution empowers organizations to meet legal compliance and protect sensitive information. Additionally, advanced technology secures data, assesses risks, implements robust security controls, and provides audit evidence through centralized log collection and reporting.
SOCSOTER AS YOUR VENDOR
Tailored services to meet the specific needs of each client with the benefits of a managed cybersecurity solutions.
ready to get Started but Not Sure How?
Can you answer these questions?
ONE-SIZE-FITS-ALL DOESN’T cut it!
Instead, EXPERIENCE SOCSOTER SOLUTIONS, built with you in mind.
Recognizing that each organization has distinct needs, SOCSoter focuses on fostering long-term partnerships rather than just selling managed cybersecurity products.
WHAT ARE YOUR NETWORK NEEDS?
Does your network infrastructure meet your clients’ needs & industry best practices?
Ensuring all network assets are accounted for and secured is critical. Do you have a process in place?
Keeping track of devices not always connected to the network can be challenging; how do you address this?
DOES ANYONE remote work?
Do your clients rely on any cloud applications for business operations?
Have you used multiple platforms to manage & monitor your various SaaS applications?
Are you monitoring the performance & security of the SaaS apps your clients use effectively?
HOW DO YOU SECURE DEVICES?
Do you handle security threats on individual devices like laptops and desktops?
Phishing and malicious sites can bypass some services—what methods do you use to detect them?
How many steps does it take to facilitate remediation that reduces incident spread & minimizes impact?
ARE YOU MANAGING RISK?
Do you have processes in place for prioritizing and addressing vulnerabilities after scanning?
What steps do you take to continuously monitor and reassess vulnerabilities beyond the initial scan?
How do you track and address vulnerabilities once they’ve been identified by your scans?
CLIENTS WITH SENSITIVE info?
How do you currently manage compliance documentation & reporting for audits?
Do you have a solution that offers 24×7 SIEM monitoring to meet regulatory compliance requirements?
What difficulties are you encountering with keeping up with & implementing compliance requirements for your clients?
24/7 Security Operations Center
Human-Powered Threat Hunting
Break free from the limitations—with a 24/7 squad of human experts, you gain the ultimate weapon in the relentless battle against today’s cyber adversaries.

designed to grow with your business
built for partnership at every step
We’ve trusted SOCSoter since the beginning, and they’ve had our back more times than I can count. They don’t hesitate to hop on the call with us and our clients to make sure they understood and felt secure. They make us look good.
Tom S.
Indianapolis, IN
Partner Since 2016
SOCSoter has been awesome to work with. Their team is super responsive—I can call and actually talk to a real person. Even though we’re not a huge customer, they always treat us like we’re a priority. Honestly, can’t say enough good things about them.
Steven P.
Utica, NY
Partner Since 2018
Compliance audits so much easier for us with SOCSoter. We are organized and ready, so when it’s time for an audit, there’s no stress on our end. It’s been a huge help in making sure we and our clients stay on track and we have everything we need to prove adherence.
Jessica M.
Gainesville, FL
Partner Since 2021
Frequently Asked Questions
Can a Small Business afford cybersecurity solutions like enterprises do?
Much like insurance, it is safer and smarter to pay a little each month instead of facing the crippling repercussions of a successful cyber attack.
I am too small and don’t have anything attackers want, why do I need this?
Your networks might provide a backdoor into a larger company’s network. A small HVAC company caused the Target breach. Your network devices, computers or servers could be used to attack other networks around the world.
I have Firewalls and Anti-Virus, why do I need anything else?
Most all organizations that have suffered a breach or significant successful attack have had firewalls and Anti-Virus. The difference between a nonissue cyber event and a reportable breach is an organization who consistently monitors their technical assets, performs log analysis and responds quickly to low level cyber hygiene issues.
If we get hit with Ransomware we can just restore from backup, right?
Yes, that will eliminate the Ransomware and get your systems back online. Keep in mind, Ransomware gangs steal all the data they encrypt, so although you are backup up your data is still gone. Also, when you restore from backups you are just as insecure as you were prior to the attack, it can happen again.