Dual-Layered ENDPOINT PROTECTION
Backed by an in-house 24×7 US-based Security Operations Center, we bring you Dual Layered Endpoint Protection. Advanced threat detection & response technology that ensures cyber hygiene & regulatory adherence. A streamlined, server-less endpoint agent seamlessly integrates, providing comprehensive protection.
With state-of-the-art technology, our SOC transforms threats into actionable insights, offering a secure environment where security is our commitment.
Endpoint | Network | Cloud | Vulnerability | Compliance

Built for devices. Designed for resilience.
ENDPOINT security Elevated
WITH A DUAL-LAYERED APPROACH
SOC Managed Security with Endpoint Detection & Response (EDR) enhances the defense & response capabilities along with meeting compliance requirements seamlessly.


an INTELLIGENT endpoint strategy
combines compliance with DEVICE PROTECTION
Experience Dual-Layered Strength
INNOVATIVE STRATEGY
To meet the needs of evolving threats & emerging regulations, the endpoint agent with dual-layered protection automatically updates to address those challenges.
CUSTOMIZABLE DEFENSE
Expert team available around-the-clock to create custom rule sets that are tailored to specific endpoint threats.
INDUSTRY LEADING
As an innovative & customizable platform; SOCSoter is able to implement features & functionality traditionally missing in other endpoint security solutions that don’t consider compliance requirements.
This reduces the overlap with your in-depth defense strategy.
HUMAN-LED OPERATIONS,
Technology-Powered EDR
When device THREATS EVOLVE,
YOUR SECURITY SHOULD TOO
24×7 SOC Managed & Curated
Complete Coverage for both workstation & server operating systems
Human-Led Proactive Threat Hunting
Opt to use your existing endpoint solution (BYOE Device)
Lightweight cross platform agent: Windows, Linux, & MacOS.
Analyzes & monitors logs to process any data the partner wants visible to the SOC
Digital Forensics & Incident Response (DFIR) built for hybrid environments
Growing & evolving rule sets based on custom searching for compromise indicators
Analyze user click data activity of past 14 days

an All-in-One Powerful Agent
endpoint Compliance
Effortless cyber Hygiene
Comprehensive server-less endpoint agent designed to simplify security hygiene & ensure regulatory compliance. This all-in-one agent installs on workstations & servers across Windows, Linux, & MacOS, leveraging the power of the SOCSoter centralized portal.

INCIDENT RESPONSE & REMEDIATION
Effortlessly manage & maintain incident response on your schedule with remote access to EDR agent commands within the partner portal, gaining control & accelerating remediation. Reduce incident spread & minimize impact, eliminating the need to wait for multiple parties to facilitate remediation.
THREAT SCENARIO
ENDPOINT INCIDENT RESPONSE CAPABILITIES
Employee clicks on a malicious email attachment and computer starts showing signs of ransomware
SYSTEM ISOLATION
Blocks connection to destinations beyond its network. Facilitating investigations, remediation, & network resumption.
Employee clicks a pop-up ad claiming software needs an urgent update; accidentally installing spyware
KILL PROCESSES
Users check a list of active processes for termination. Identify & stop potentially malicious processes or those causing network denial of service activities.
Employee falls for an email that mimics a legitimate login page and accidentally leaks credentials for unauthorized access to accounts
LOG OFF USERS
Rapid log-off all users posing a threat to the system / network. Gives administrators a chance to enhance authentication to ensure only legitimate users have access.
Employee has work bag containing devices with sensitive data stolen which leads to exploit and/or misuse of sensitive data
KILL PILL
Remotely request all data from the system to be wiped & reset windows back to default. Missing data could be costly if it causes a regulatory investigation / infraction.
ADVANCED DIGITAL FORENSICS
Incident Response swiftly addresses & mitigates the immediate threat. DFIR identifies the root cause & implements measures to prevent future incidents.
Identify the origin & scope of the attack.
Pinpoint the exact entry point & timeline of events.
Gather evidence for potential legal action.
Prevent similar attacks from happening again.
Deep dive to understand the “how” & “why” behind the security breach with Dual-Layered Endpoint Protection
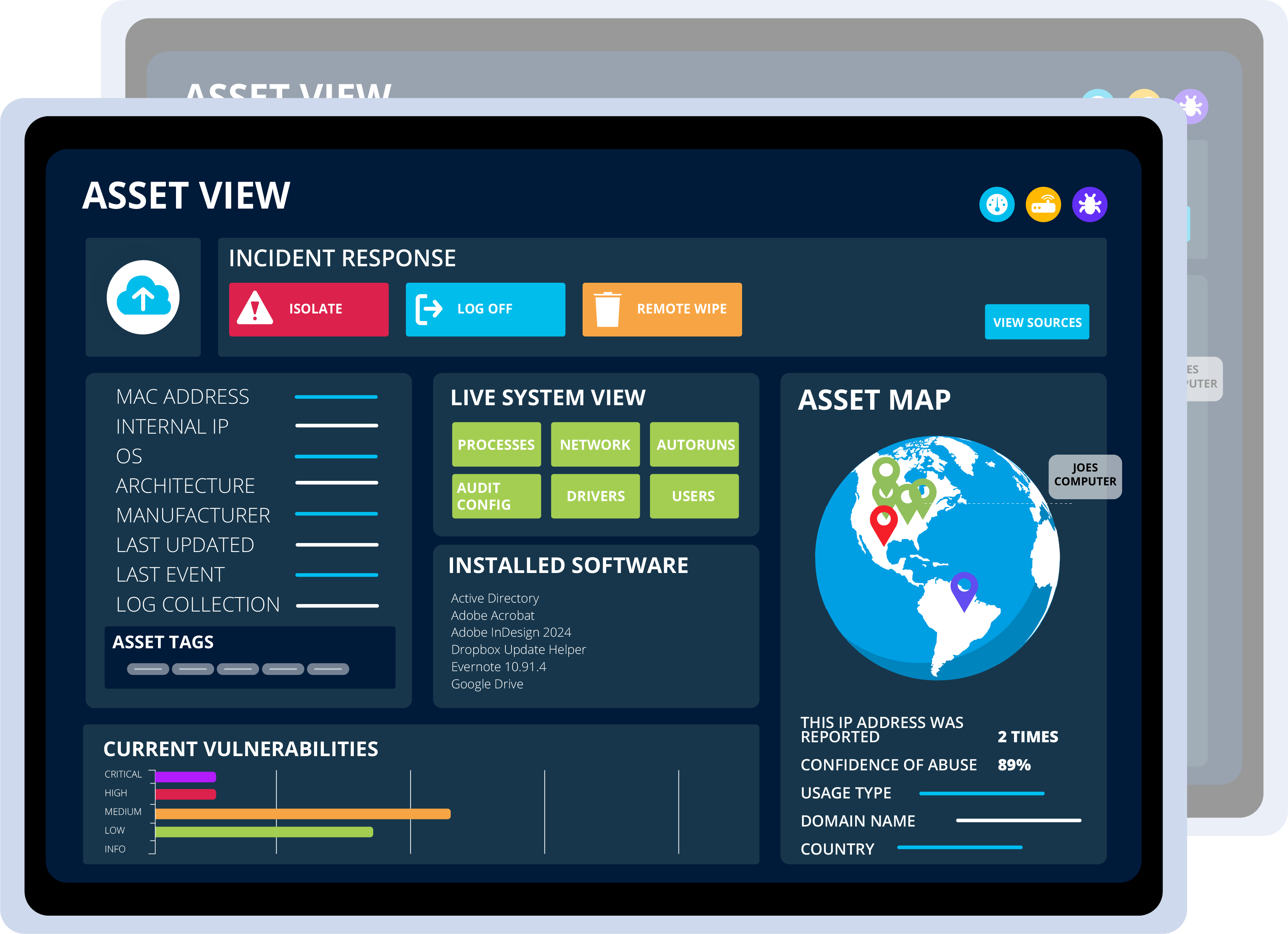
metrics dashboard
Dual Layered Endpoint Protection is putting you in control! With complete visibility into endpoint activity, you can make informed decisions & enforce security policies effectively to address risk.
scheduled tasks
View all scheduled tasks on endpoints to spot any unauthorized changes or suspicious scripts that may be utilized for malicious intent.
running processes
Monitor endpoint processes to identify suspicious activity, potential malware, & unauthorized applications.
network connection
Monitor all network connections to & from your endpoints to detect unauthorized communications, data exfiltration risks, & potential malware channels.
installed software
Maintain a complete inventory of all installed software on endpoints. Identify unauthorized installations, outdated software with known vulnerabilities, etc.
VULNERABILITY MANAGEMENT
Focus on Risk, Not Just Detection
prioritize what actually Matters
Evaluating all assets
With ongoing evaluation of your systems, vulnerabilities, & configurations, automated scans & reviews ensure that your security measures are up-to-date & resilient.
COMPREHENSIVE SCANNING
Our robust VMS scanning goes beyond basic detection, meticulously examining your endpoint security to identify all known software vulnerabilities. No gaps remain in your defenses.
Continuous Assessment
Gone are the days of waiting for outdated vulnerability scans. SOCSoter provides near real-time vulnerability assessment, giving you immediate insights into the security posture of your endpoints.
configuration compliance
security content automation
Take the guesswork out of your compliance requirements with our innovative Security Content Automation Platform (SCAP)-compliant capability.
Automated Discovery
Using SCAP technology to automate system configuration discovery & policy compliance checks, eliminating manual audits & saving time & resources.
Customizable Benchmarks
The portal allows you to choose specific compliance benchmarks such as DISA STIGS & CIS Benchmarks for tailored system evaluation, because one size does not fit all.
Actionable Reports
Assessment results are shown in the portal for easy identification of deviations from best practices & prioritization of remediation for a custom compliance & hardening program.
take complexity out of Dual Layered Endpoint Protection
EXPERIENCE HOW THESE EDR CAPABILITIES ADD THE + FACTOR TO YOUR SECURITY
See What’s Missed, Stop What’s Coming
endpoint Defender
Double Up Your Defense
SOCSoter’s Endpoint Defender technology goes beyond basic protection, building upon the strong foundation of Endpoint Compliance. Dual Layered Endpoint Protection is empowering you to see what you missed & stop what’s coming, and keep your organization a step ahead of attackers.

Endpoint Detection & Response (EDR)
No EDR solution can replace all other security solutions such as Network Monitoring or Antivirus.
Endpoint Detection & Response (EDR) helps along with these solutions by tracking, monitoring, & analyzing data on endpoints.
soc managed security
Our 24/7 SOC managed security solution monitors endpoints, identifies vulnerabilities, & efficiently manages resources, ensuring security inside & outside your network.
comprehensive protection
SOCSoter’s EDR provides critical defense against cyber threats by analyzing applications, processes, network connections, registry changes, & policy violations to ensure comprehensive protection.
threat detection
The EDR’s robust rule set swiftly detects malicious activities, continuously refined by security experts to stay effective against new threats & reduce false positives.
continuous improvement
Continuously update EDR’s rules & detection based on evolving threats, enhancing effectiveness & minimizing false alarms, ensuring seamless operational continuity for your organization.
Protecting all connected devices from malware, ransomware, & unauthorized access with Dual Layered Endpoint Protection
centralized Log Analysis & Monitoring
The log storage service securely stores logs for compliance with regulations, allowing long-term storage of security events, application logs, and system logs in an encrypted format.
SECURITY, ANYWHERE & EVERYWHERE
Collects & analyzes security event logs from Windows, Linux, & MacOS endpoints, providing a centralized view of organizational activity. SOCSoter’s EDR agent enables log collection, storage, & analysis on any device with the agent installed.
REMOTE THREAT DETECTION
Even when devices are remote, valuable security insights can be gained through comprehensive log analysis. This advanced monitoring detects signs of compromise, misuse, & policy violations, bolstering threat detection & response.
Analyze Trends
Identify Patterns
Pinpoint Attack Start
to understanding its root cause, & identifying potential vulnerabilities.
EXTENDED DATA RETENTION
Storing agent activity for 1 year! Crucial for piecing together the timeline of attack. In-depth forensic analysis of past incidents yields valuable insights into the behavior.
PROACTIVE THREAT HUNTING
Extended storage allows for threat hunting to proactively search for indicators of compromise that might otherwise go unnoticed.
MEET COMPLIANCE REQUIREMENTS
Endpoint Detection & Response (EDR) is rapidly becoming a requirement for regulatory compliance. Many now mandate EDR solutions with long-term telemetry data storage (often 6 months or more).
Agent-Based Telemetry Collection
An approach that identifies & neutralizes threats before damage. Storing security data in the centralized portal aids in compliance audits by showing adherence to EDR storage requirements to auditors.

Did you know?
Most phishing or malicious website blocking services only stop what they know… but what if they don’t know yet?
…
socsoter is providing an industry-first, 4th weapon to add to your phishing defense
PHISHING DETECTION & RESPONSE
DEVELOPED BY SOCSOTER
A Comprehensive approach to identify click threats that may bypass traditional defenses
A Powerful Ally to compliment your prevention
Phishing Intelligence is not meant to replace any phishing prevention tool you already have! Phishing Intelligence complements existing phishing prevention tools by detecting frequently accessed fraudulent links quickly, addressing the challenge of keeping up with hackers creating new domains.
GLOBAL PHISHING DATABASE
Using advanced analytics & machine learning, we compare customer click data with endpoint agent log data to identify patterns & anomalies, enabling detection & response for user & data protection.
When a new bad phishing site is added to the database, threat intelligence looks back through previous customer click data to compare key sites & identify potential matches for remediation.
historical analysis
Historical Analysis references the extensive database to analyze click activity from the past 14 days to enable response. Designed to remediate all previous & current affected users the moment phishing is detected to enable incident response.
Enhance your defense strategies against evolving:
- Phishing
- Click-Jacking
- Malvertising
- Quishing Links (QR Codes)
- Malicious Links In Documents

With historical context of a link or domain, we can review what might have been innocent in the past but is now known to be malicious.
threat search
Threat Search feature uses our threat intelligence dashboard to continuously search for indicators of compromise (IOC) or bad sites that have been collected over time.
There are millions of IOCs visible to you in the database today. The database is constantly growing & more data means better detection!
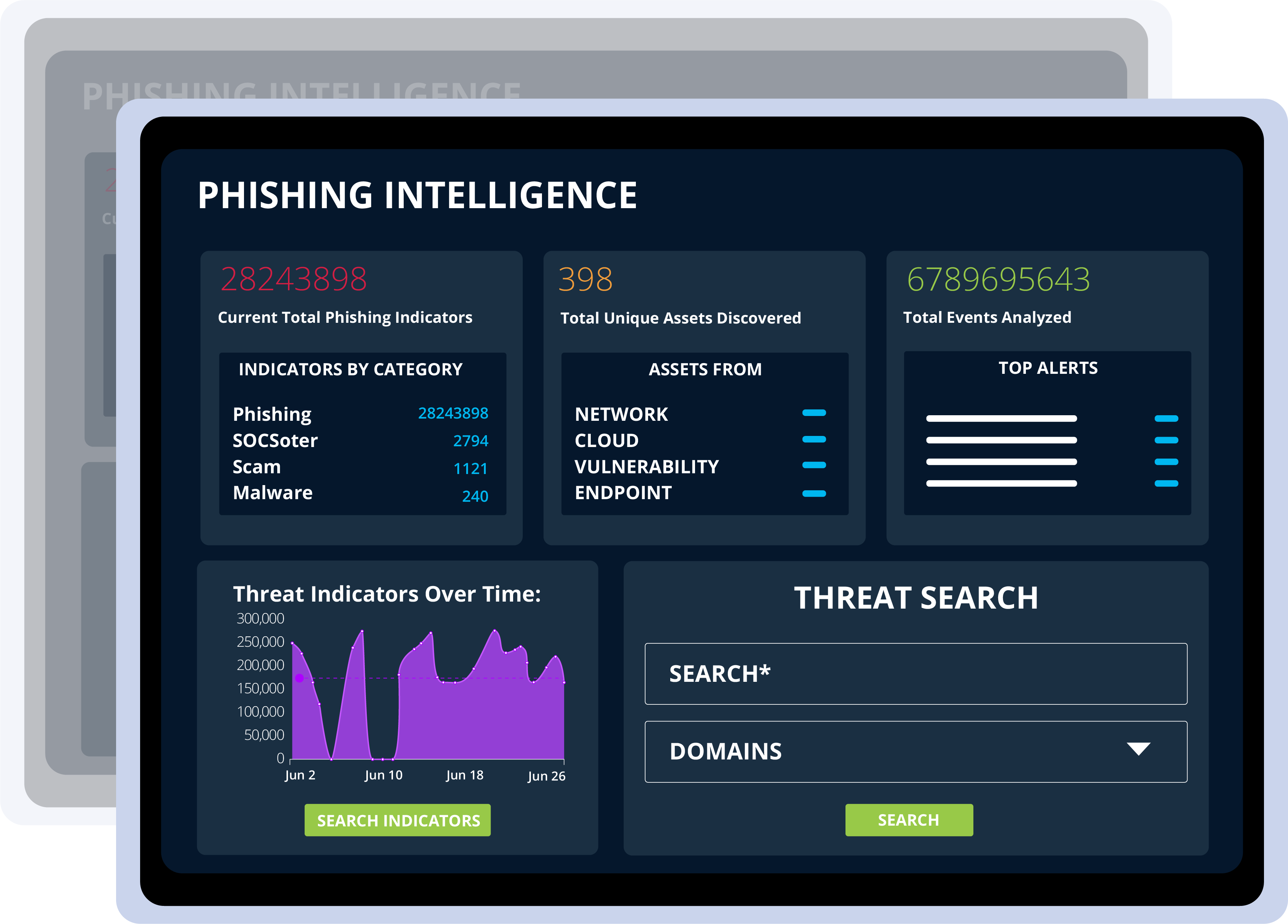

Search domains to see if it has been reported as malicious at any point with a safe way to view the site through real-time screenshots.
*If there is a domain that looks suspicious but hasn‘t been flagged previously, you can push it forward to the SOC for immediate review!