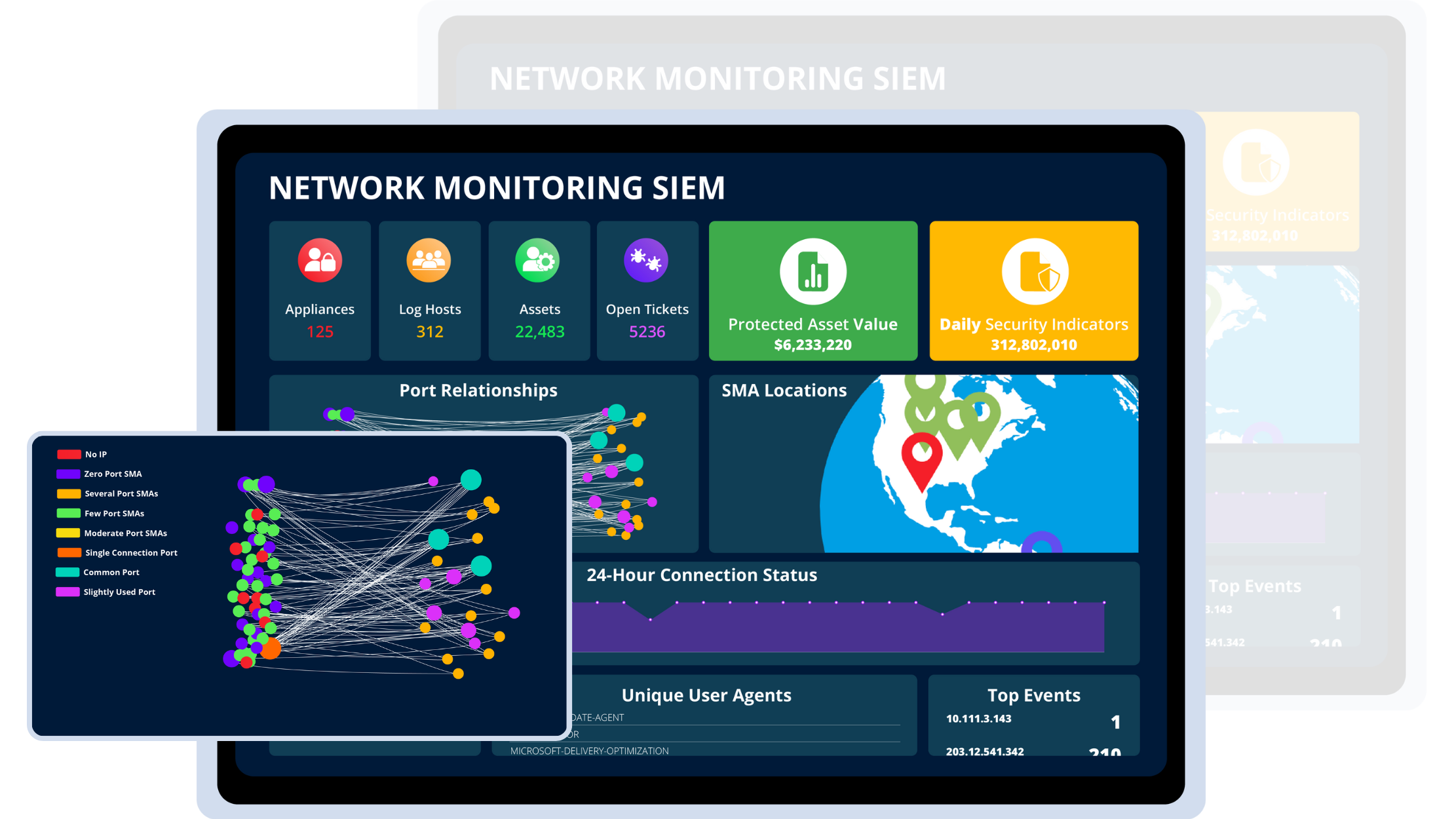
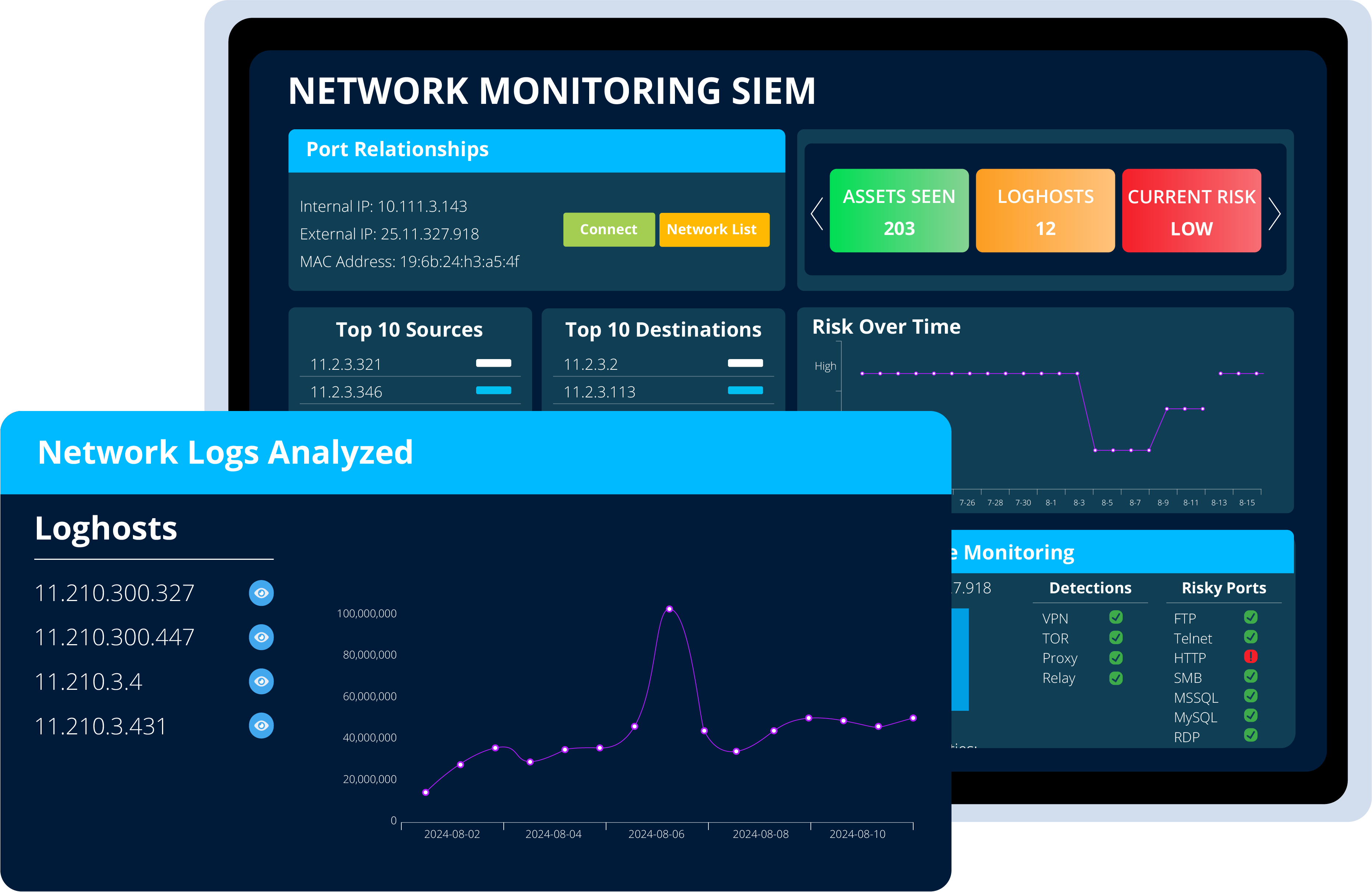
Multi-Tiered network monitoring siem Technology
Our Network Monitoring SIEM Technology conducts real-time network analysis through asset insights, packet inspection, protocol analysis, syslog data, and executable analysis to proactively detect and address threats and misconfigurations that may lead to breaches.
Swiftly detect threats and intrusions to your organization. Network Monitoring SIEM Technology paired with our Threat Intelligence allows advanced 24/7 Managed Security Operations to conduct real-time network analysis and threat hunting supported by expertly trained and certified security engineers.
Endpoint | Network | Cloud | Vulnerability | Compliance

Built to be versatile. Designed for range.
NEXT LEVEL network MONITORING
cutting-edge siem technology

NETWORK MONITORING

SIEM TECHNOLOGY
Network visibility like you’ve never seen before!
limitless coverage in real-time
Gain exceptional visibility by integrating, normalizing, and analyzing data from multiple sources (signals), allowing you to understand system connections and identify security issues impacting an organization. Network Monitoring SIEM Technology safeguards your infrastructure, streamlines compliance, & provides 24/7 threat detection.
Network based threat analytics
Covering aspects of all, but deployed within, the context of real risk. Signal to noise ratio reduction backed by 24×7 expert human analysis.
complete coverage
Coverage of the most complex networks; for on-premise, multi-location, &/or virtual environments to identify threats from or to any device connected to the network.
industry Leading visibility
As an innovative & customizable platform; SOCSoter is able to implement features & functionality to provide a holistic view of the complete network.
Find the devices you never knew existed or nobody told you about!
HUMAN-LED OPERATIONS,
Hardware Driven Protection
enhance your network visibility
beyond device level defenses
Cyberattacks within the network are critical to detect quickly, making it crucial for organizations to maintain a comprehensive visual representation of their network.
continuous threat monitoring
EXTENDED to your network
Identifying malicious activity and insider threats while keeping you informed of crucial discoveries. This enables organizations to continually assess their overall security architecture to determine whether they are complying with their internal information security policies or external compliance regulations.
TRAFFIC ANALYSIS
Detects potential security threats like lateral movement or large amounts of data being sent from a single device. This enables organizations to take timely and effective action to mitigate threats.
Monitor the cardinal directions of Traffic Analysis
VIEW LATERAL MOVEMENT
North-South to East-West traffic visibility, with agent-less device discovery & analysis.
Identify lateral movement, brute force attacks, privilege escalation, ransomware, command and control exploits
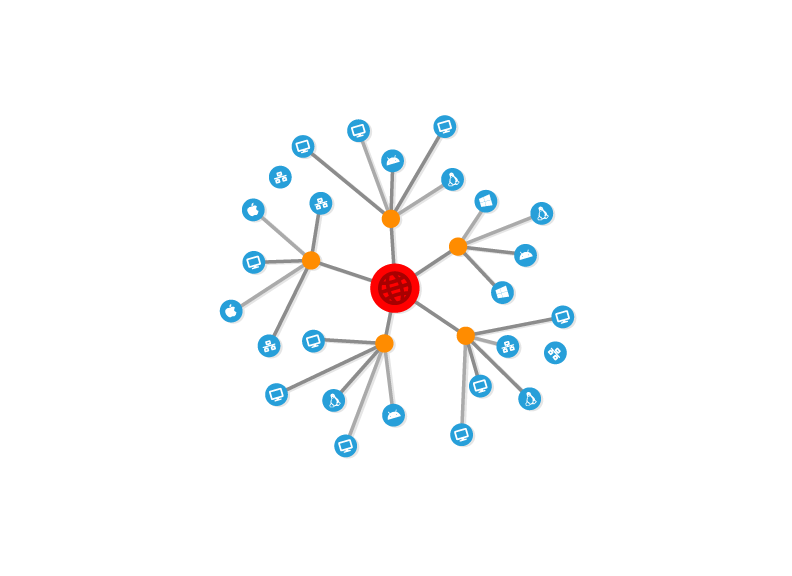
Dynamic Network Mapping
See your network in a new way
A dashboard for everything you need to view your assets, without bulky extras! Maintain an up-to-date inventory of all authorized assets; including hardware, software, external data, and network resources. Automatically updating as assets change or new ones are added.

Centralized control with
Secure Asset MAnagement
A comprehensive view of assets through automated passive discovery & inventory tracking. Integrating all key data & threat intelligence from the moment it accesses the network & extends beyond. Get a complete inventory of your network with real-time asset discovery without the need to deploy agents. Any device connected to the network gets profiled and recorded as connected.
See all assets including IoT, Medical Devices, Manufacturing systems & any other system connected to the network.
monitor the use of ports & protocols
Uncover hidden risks with continuous monitoring that detects anomalies & the use of weak, unauthorized or insecure applications, ports & protocols.
Automated asset details
Track assets & the associated software they use on the network, identify their operating system, hardware & other unique features to identify them on the network when you need to most.
identify unused, unknown or unmanaged devices
Eliminate blind spots by pinpointing inactive, unidentified, and unauthorized devices on your network.
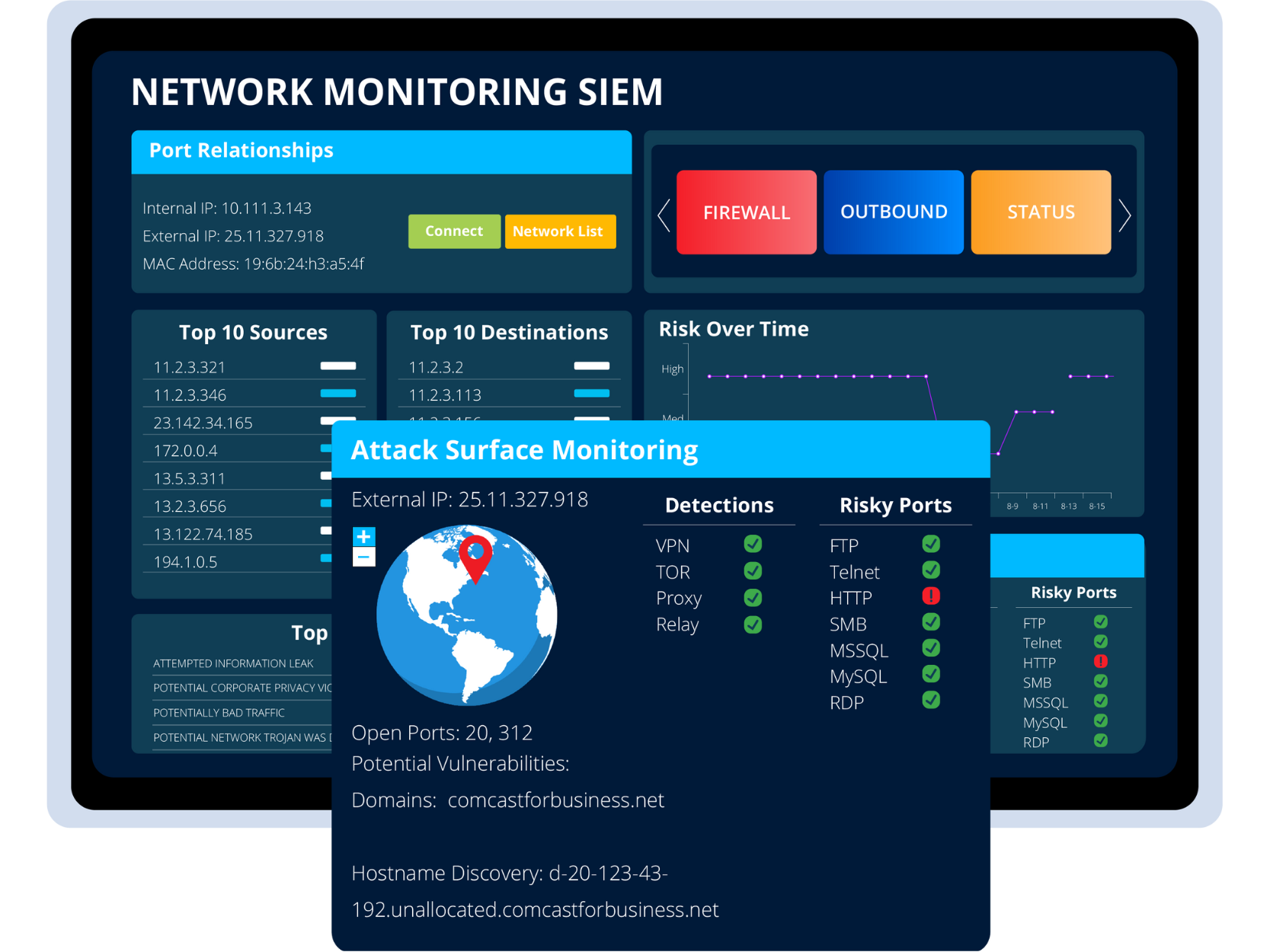
reduce your attack surface
The external hacker view
Cyber threats can come from anywhere, making it essential to have a holistic view of your security posture. SOCSoter is actively identifying new & emerging risks, including any risky open ports and exposed vulnerabilities on the firewall.
Expose, disrupt, & respond to threats outside your perimeter.
Managed Assets
3rd party assets
guest assets
Shadow IT
Monitor devices
Coverage of external IP address use, expired certificates, & management interfaces exposed to the internet.
visualize exposure
A comprehensive view and monitoring of all internet exposed services to help you stay secure.
The Hacker view
Incorporate an approach to security that continuously identifies & monitors points of attack as seen by potential attackers.
Attackers go beyond THE perimeter, shouldn’t your security too?
Identify risky exposures
SOC analysis into external asset exposures that could enable attackers to breach the network.
patch Management support
Receive alerts for patch management requirements against vulnerabilities in network infrastructure commonly overlooked.
Monitored for risk exposure
Know if the network is being used as a spam gateway, TOR routing, relays, proxies or has insecure services running.
Behaviors Beyond the Perimeter
Views into all user activities to detect any unusual or suspicious actions, such as port changes in the firewall – new or risky.
External Vulnerability Detection
Attack Surface Monitoring
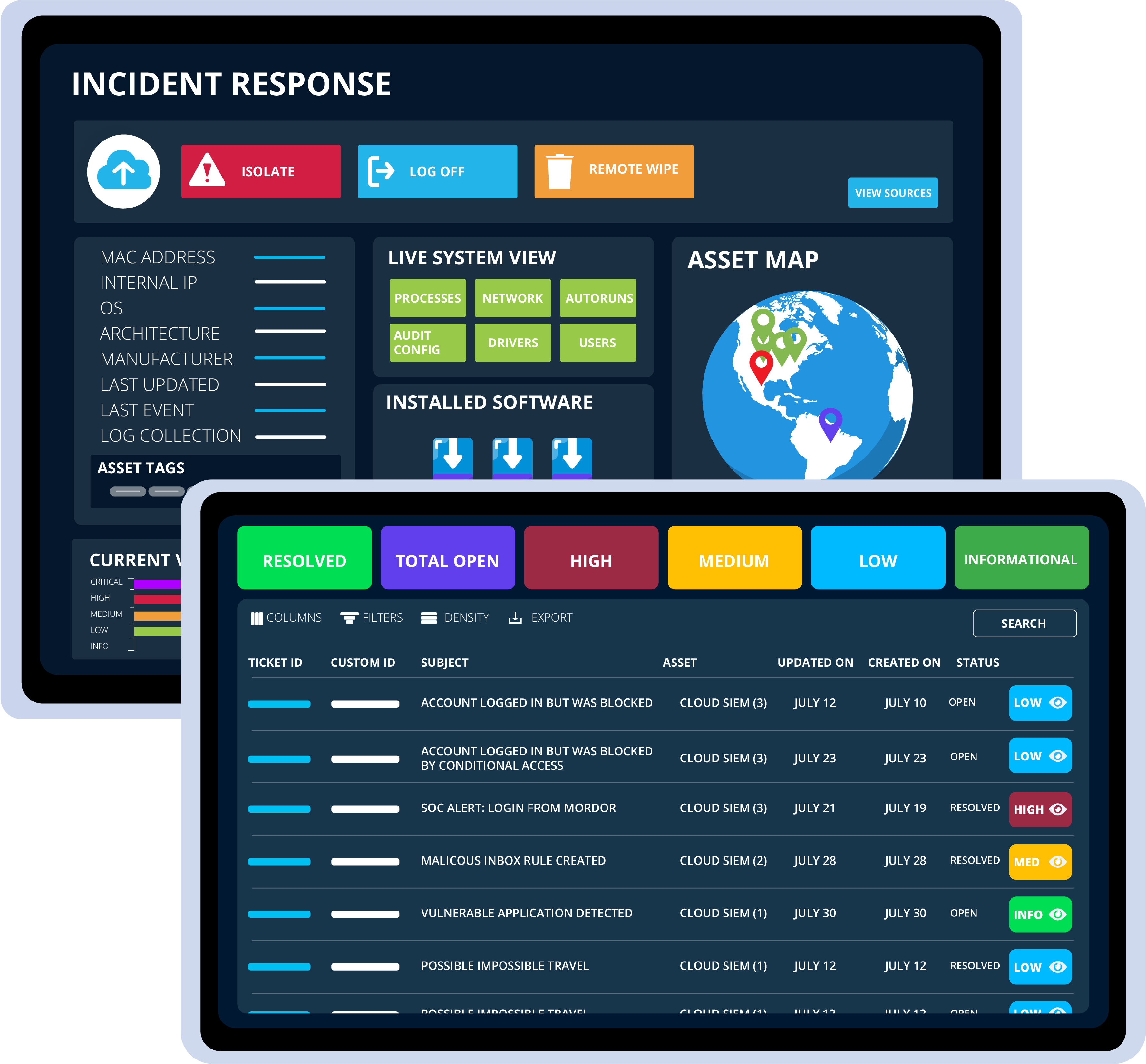
A central location that encompasses all points of potential exploitation, both internal & external. High context investigative timelines detail attack techniques, impact, and recommended response in a single view.


security information & Event Management
Device-Centric analysis
with SIEM Technology
Eliminate the need to navigate between multiple products by correlating relevant logs with metrics in a centralized platform for on-prem and virtual environments.
Change how you view assets & investigate network anomalies
with Advanced Threat Hunting Tools!
Real-time Threat hunting
enabling incidence response
Continuous monitoring of network activity enables real-time detection of any abnormal behavior and potential threats, empowering you to respond promptly to security incidents.
a proactive approach to mitigating security incidents
Offering rapid detection, containment, investigation, & recovery from security breaches. Swift contact tracing through continuous monitoring of authorized & unauthorized assets
go beyond edr
to secure your entire infrastructure
EDR is a critical tool, but not a standalone solution. Secure your infrastructure by pairing EDR with other security measures to create a robust, multi-layered defense.
EDR focuses only on endpoints like desktops, laptops, and servers, leaving gaps in coverage for network devices, cloud services, and IoT devices, which attackers can exploit.
RELYING ON EDR ALONE
WITH NETWORK VISIBILITY
IOT DEVICES
NETWORK DEVICES
VIRTUAL DEVICES
OUTDATED SOFTWARE


DEVICE MISCONFIGURATIONS



MALWARE INTRUSIONS



LOST/UNKNOWN DEVICES



POLICY VIOLATIONS



PORT SCANS



UNUSUAL APPLICATION USAGE



These gaps leave critical areas vulnerable to exploitation by attackers. The limited visibility into the broader infrastructure challenges threat correlation, making it difficult to detect and respond to complex, multi-vector attacks.
Network Malware Forensics
investigating data in motion
The network monitoring appliance scans network files for malware by comparing them against known malware databases and then examines metadata, file origins, transfer protocols, & file hash for signs of compromise.
Advanced Malware Scanning
The appliance scans network traffic for malware using threat intelligence feeds to detect known malicious files based on their signatures.
Metadata Analysis
We don’t stop at just the file itself. We analyze file metadata; creation date, author, and modification history, to uncover any discrepancies.
Investigate in seconds!
Speed up and simplify investigations with real-time SOC collaboration.
CUSTOM RULE-BASED ESCALATION
tailored TO SPECIFIC ENDPOINTS
SOC team creates specific rules to guide prioritization of threats by possible outcomes. Gain deep visibility into the root cause and attack path of security incidents.
- Ensures a measured response based on the specific circumstances.
- Custom rules can be configured for different device types (e.g., desktops, servers, mobile devices) to ensure the appropriate responses

POLICY-BASED ALERTING
AT THE NETWORK & APPLICATION LEVEL
Analysts are able to recall network data, logs and other telemetry to perform in-depth forensic analysis of any event. Simplify investigations with 24×7 expert incident analysis that concentrates on critical alerts.
- Ensure proper configurations, handle vulnerabilities, & stay updated.
- Minimizing false alarms to eliminate alert fatigue
- Custom alerting escalations tailored to your unique environments.
50x faster than using unmanaged, out-of-the-box SIEM solutions alone!

Let the SIEM do the work for you!
A fresh perspective on hardware based Network Monitoring SIEM Technology with detections approved by experts, & DFIR tailored for hybrid environments.

A complete visual representation of ALL devices on the network
All authorized & unauthorized assets go through the SOC-SIEM platform
View communication pathways between devices
Identify devices by OS and IP/MAC addresses
Network map can be manipulated for a closer look
See each asset more fully by clicking on the asset
Reporting and exports Enable easy delivery on compliance requirements.
Improve incident response by utilizing details within the asset map
Make sense of your data
optimize data hygiene & compliance initiatives
Ensure your organization meets compliance requirements while maintaining secure and reliable access to critical log data.
Network Monitoring SIEM functions as a centralized syslog server, enabling organizations to send and manage a wide variety of logs—from firewalls, switches, routers, WiFi, to servers (Windows/Linux)—all through a single interface.
These logs are continuously monitored, analyzed, and securely stored off-site to enhance overall security.
log collection
from any source in real-time
off-site log storage
Log data is analyzed and stored off-site for improved hygiene and compliance, ensuring separation from other customers’ data.
Location based log separation
Log data can be stored at the device location for added flexibility based on specific retention needs or unique client requirements.
long-term data retention
log storage services offer secure, long-term retention of security events, application logs, and system logs. Typically, logs are stored for a specified retention period of 1 year, with encryption to ensure data integrity and security.
DRIVE YOUR SECURITY STRATEGY FORWARD
Ensuring your network adheres to client requirements is crucial for protecting sensitive data, maintaining trust with stakeholders, and avoiding costly penalties.






POLICY VIOLATIONS
Failure to follow asset management protocols can result in data breaches, environmental damage, & regulatory non-compliance.
Detecting & addressing violations promptly is key to safeguarding organizational integrity & reputation.
Monitoring users & systems help enforce adherence & maintain accountability.
COMPLIANCE REQUIREMENTS
Following regulations for the entire asset lifecycle, including procurement, maintenance, & disposal is required.
Organizations must ensure secure data destruction for digital assets & disposal for physical assets.
Comprehensive up-to-date documentation are key to a strong compliance program.