Cloud SaaS Security Monitoring
Risks in the cloud are like sharks in the water—unseen until they strike. SOCSoter’s Cloud SaaS Security Monitoring provides a cloud-based SIEM solution to proactively monitor third-party SaaS applications, mitigating business and cyber risks effectively. Integrations through API’s, blob and bucket data transfers allows an almost unlimited integration capability for security monitoring. Businesses face new security risks and challenges that need to be addressed in the cloud!
Combined SaaS applications with in-house 24×7 SOC monitoring to provide threat surveillance that generates events & alerts for analysis & escalation that you could not see or hear before.
Endpoint | Network | Cloud | Vulnerability | Compliance

Built with simplicity. Designed for ease.
Secure your infrastructure
with Cloud SaaS Security Monitoring

MANAGED CLOUD INFRASTRUCTURE

SIEM FOR THE MODERN WORKFORCE
Control your SaaS Security Risk
with a cloud SIEM solution
Secure your network with advanced threat intelligence, providing a centralized hub to detect, prioritize, and resolve security incidents, while ensuring compliance with regulatory mandates.
Single, collaborative SIEM platform
Monitor the applications you are already selling! Centralize & streamline security event management by consolidating all API components & tools.
Multi-Cloud Protection
Enhance your hybrid cloud adoption and digital transformation initiatives by implementing cloud-native collection and detection methods to address emerging threat landscapes.
Cloud-Native Architecture
Our Security Information and Event Management (SIEM) system offers multi-tenant scaling and elasticity, enhancing SOC efficiency for security and IT teams.
Adjust the scale according to your requirements.
HUMAN-LED OPERATIONS,
cloud-based visibility
Cloud SaaS Security Monitoring
of the entire infrastructure
Seamless integration to bring your full stack of cloud services into a single, user-friendly interface. From security tools to business line applications, streamline your cloud protection by monitoring everything in one centralized hub, maximizing efficiency and convenience for unparalleled simplicity, security, reporting and compliance.

streamlined virtual investigation
for every environment
SOCSoters’ Cloud Monitoring SIEM provides unparalleled visibility and comprehensive monitoring to ensure your entire environment remains secure and efficient. Stay ahead of potential threats and ensure continuous protection of your digital assets with SOCSoters’ cutting-edge monitoring solutions.
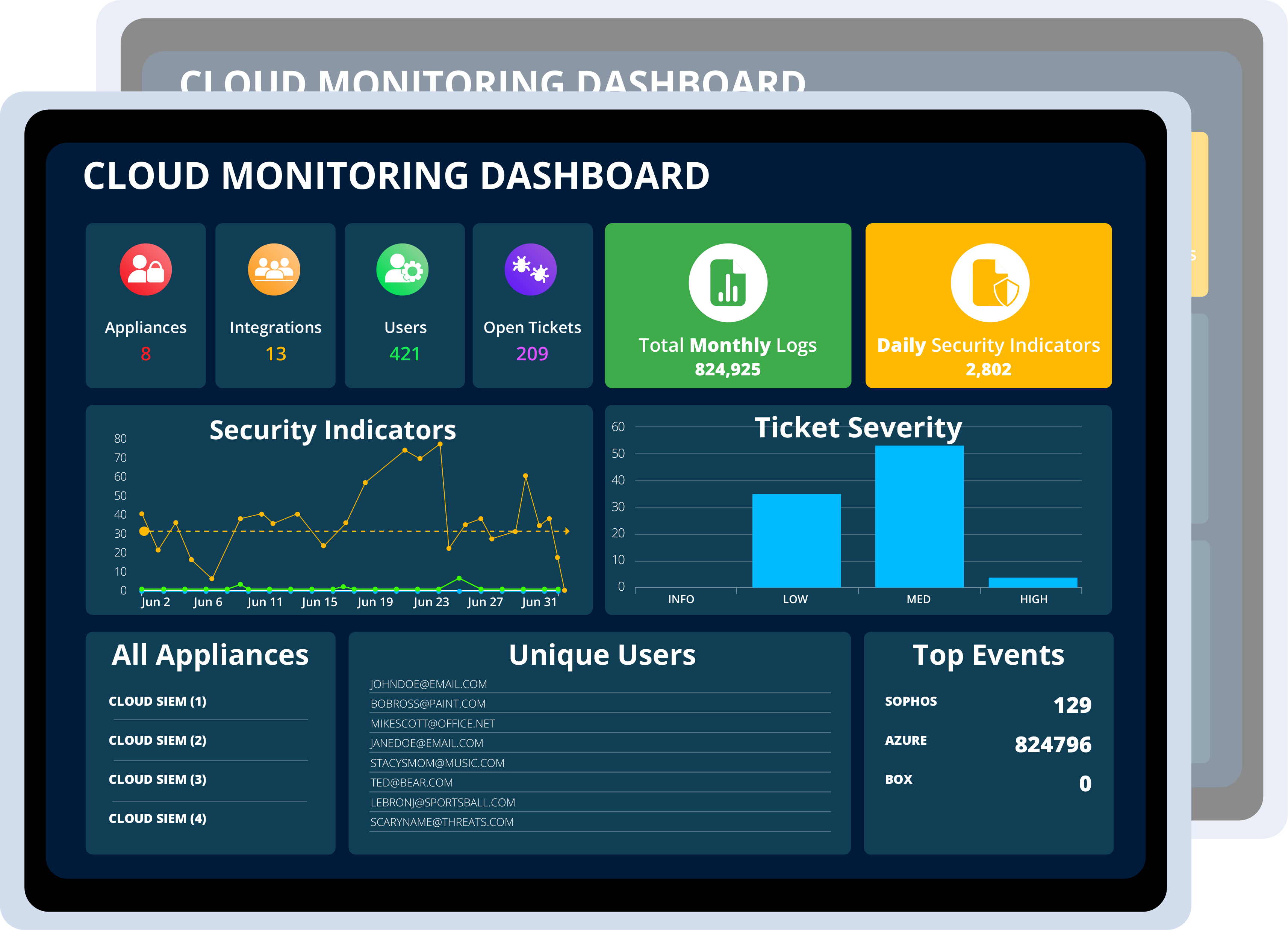
Summary of Total Logs Collected over the last 30 days
Summary of Total Security Indicators for 24 hours
Categorize Tickets based on Severity for prioritization
View the Top Event Generator producing the most events
Updated list of Unique Users being presented within logs
List of all Cloud SIEM Appliances & quick dashboard access
Status of all resolved & unresolved Security Indicators
Access to Open Tickets to view, organize, & export tickets
ticket Status Tracking
Monitor, manage, & resolve open tickets efficiently by categorizing & exporting by severity level. Access detailed information including ticket & alert details, affected asset, timestamps, & current status, ensuring no issue goes unnoticed.
STREAMLINED INVESTIGATION
Supports organizations with server-less environments or distributed workforces. Collecting event data from cloud-based data SaaS applications, to provide real-time security insights with robust custom detections and multiple auto-updated dashboards.
Comprehensive Insight
Visualize metrics, activities, logs, & more across your cloud environments effortlessly from a single interface. Collect all your logs affordably, perform analytics, & only pay to retain essential data on the platform.
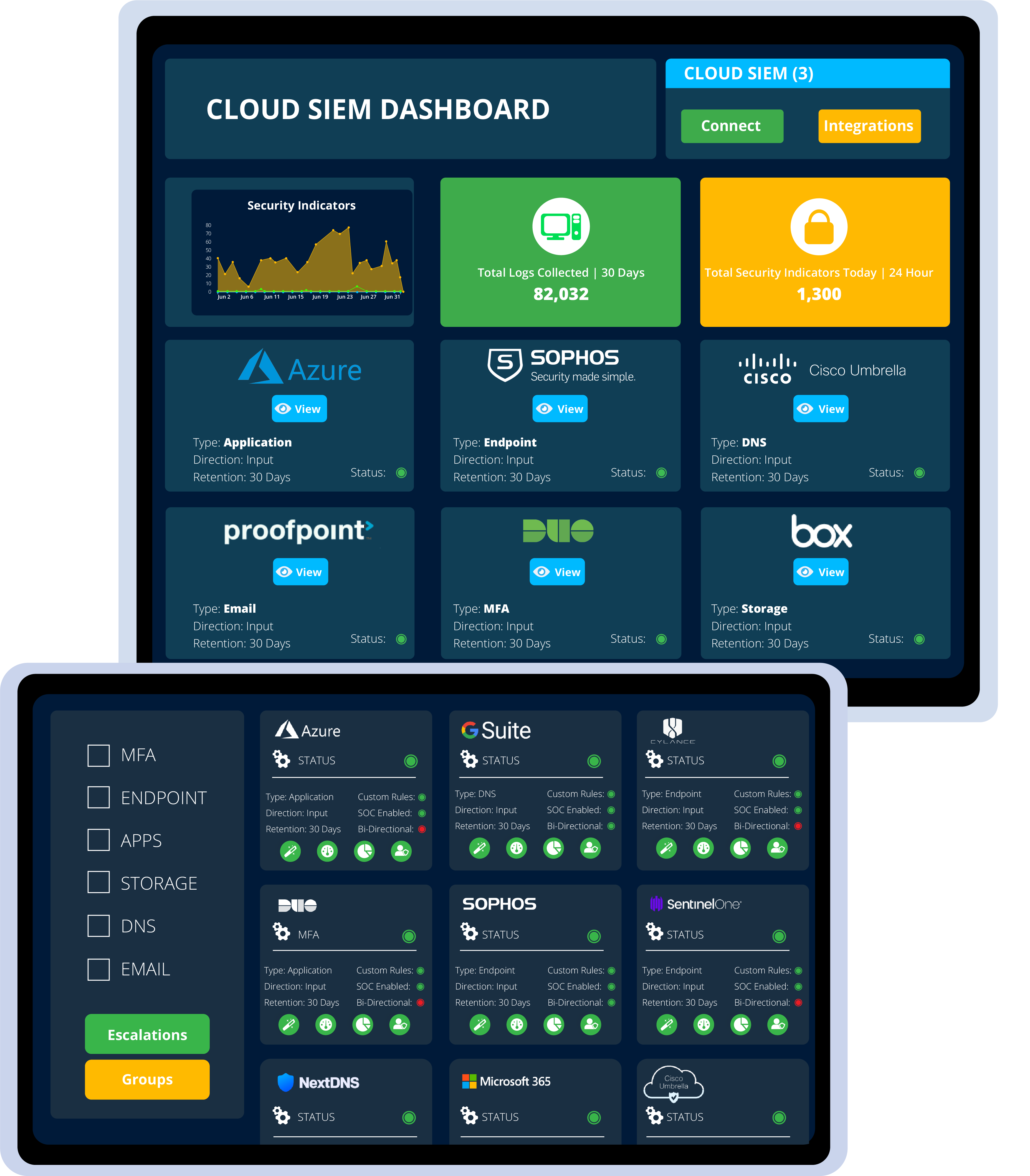
Appliance-based count of Total Logs Collected
View Total Security Indicators for the last 24 hours
Consolidated view of all Integrations & deployment status
Status of resolved & unresolved alerts based on date
reduce the noise
Streamline all your data to consolidate alerts & create rules in an intuitive dashboard. Prioritize alerts to minimize log events & prevent overload.
Utilize threat intelligence & behavior analytics for alert prioritization.
Parse, map, and normalize both structured and unstructured data.
Correlate detected threats to reduce log events.
Configure threshold-based alerts to prevent overload & false positives.
Leverage Your Existing Solutions!
Gain full visibility into your modern applications
Streamline access & enhance visibility by bringing together diverse data into a single, cohesive view.
Cloud SaaS security monitoring means making informed decisions faster, enhancing collaboration, & maintaining a comprehensive overview of your operations, driving better strategic outcomes & boosting overall productivity.
Elevated Monitoring Starts With
the power of integration
Seamless Visibility Into Cloud-Based SaaS Application Misusage or Policy Violations
Unlimited API integration with third-party tools and technologies allows for a easy flow of real-time information between different environments. Access to metrics and resources specific to each integration.
Two-Factor Authentication
Endpoint & Single Sign-On (SSO)
Business Line Applications
Security Tools
SaaS and Cloud providers
Automation tools
Ticketing Solutions
Databases & common server components
Comprehensive visibility into the performance, security, & ownership of all APIs. Identify & prioritize the most at-risk areas for remediation in a central location.

























LIVE LOGS & REPORTING
CONSOLIDATED METRICS
CUSTOM RULES & ALERTS
THREAT INTELLIGENCE
Monitoring Cloud infrastructure
Security analysts and SOC managers gain enhanced visibility across the entire infrastructure, enabling a comprehensive understanding of an attack’s scope and context. Streamlined workflows automatically triage alerts, swiftly detecting both known and unknown threats.
Threat Intelligence
Cloud SIEM delivers advanced threat surveillance with a refined list of malicious IPs, URLs, and domains to assess threat severity. By contextualizing log data, it helps prioritize critical indicators and enhance security posture.
proactive threat hunting
SOC engineers hunt for threats on all SaaS platforms, identifying indicators of compromise to strengthen defense against cyber attacks. Continuously monitoring for suspicious activities like failed logins or unauthorized credential use to detect & address threats promptly.

US-BASED SOC MONITORING
24×7 expert oversight of your cloud data, ensuring robust protection against cyber threats. Rapid response to detect vulnerabilities early & reduce risks. The SIEM allows SOC engineers to proactively threat hunt for indication of advisories across SaaS platforms.
User & Entity Behavior Analytics
Leveraging sensitive data signals from logs, network traffic, and endpoint data to establish a baseline of normal behavior. It then monitors activity across the network, detecting suspicious behavior by identifying deviations from this baseline.
IN-HOUSE DEVELOPMENT
Our in-house development team provides customization, security, agility, and enhanced control. Tailor features to your specific needs and workflows for better security protocol management.
Streamline collaboration between developers, security, and IT teams by providing shared threat insights expediting security inquiries within a unified platform.
Unique RULE sets & Correlation
Custom detection rules to extend your coverage based on unique aspects of your environment. Developed for each integrated service to generate cyber relevant events & alerts for effective analysis & escalation.
rule-based threat detection
Rules sets are updated continuously to identify threats, set alerts for suspicious activity, monitor permission changes, & auto-lock accounts after failed attempts.
Detections are aligned to the MITRE ATT&CK® framework
Custom features & functions to match your environment & business workflows.
Access to our team ensures best practices which is beneficial for sensitive data & compliance needs.
Keep pace with rapidly evolving cloud technologies & integrate new services frequently.
Predict & respond to attacks with built-in threat intelligence & threat hunting
CUSTOM escalations
Empower your response with custom escalation capabilities to tailor responses and detections from all your services, ensuring the right teams receive the right alerts quickly!
Notify users about configuration alerts at the group, customer, or service level.
Customize alerts for specific teams & receive timely notifications for misconfigurations & violations.
SaaS is a Business Risk
you can Manage!
automated threat intelligence
built-in security rules
custom tuning & rule creation
long term log storage available
Access log data from anywhere
track unsanctioned app usage
US-Based 24×7 SOC MAnaged
In House Development
all-you-can-eat api integrations
only qualified alerts escalated
single point of access portal
user & Network threat monitoring
SaaS Security Simplified,
SIEM for the Modern Workforce
When used in conjunction with on-premise Network SIEM & Endpoint Defender, this Cloud SIEM serves to close “the security loop”, offering comprehensive protection for both on & off-premise devices accessing cloud resources.
As a stand-alone product, Cloud SIEM will monitor activity on any integrated APIs being used in the customer’s environment.
Cloud-native SIEM for cloud-native threats
Remote workforce & cloud adoption with SIEM is critical to monitor all your customers SaaS applications!
With the rapid advancement of SaaS applications, integrations, data sharing permissions, & user identities, businesses are encountering new security challenges.
Virtual offices & remote workers need secure access to corporate resources, applications, & data, enabling employees to work securely from any location, without compromising the security or performance of the network.
Designed to meet the needs of dynamic environments
Cloud SIEM systems can operate within a highly encrypted FIPS environment. FedRAMP offers Moderate, High, or Enterprise/Commercial levels to standardize security assessment, authorization, and continuous monitoring for cloud products and services.
Microsoft GovCloud is accessible upon request at no extra charge.
LOG collection
Audit logs track user activity to detect unauthorized access attempts, aiding incident response by analyzing network traffic and system events in real-time to prevent incidents from escalating.
- All reports, meta data & raw logs are provided for further analysis by customers or MSPs.
- Visualize & review security activities & generate detailed audit reports.
LOG storage
Ingesting, normalizing, & enriching logs & third-party security alerts, while monitoring, analyzing, & storing logs collected from API integrations, on-premise network data, & cloud environments off-site.
- For organizations that do not have a network SIEM or have server-less offices, a provided installable agent can be used on any system to turn it into a Syslog Collector
Use an installable agent for organizations without a network SIEM or with server-less offices, turning any system into a syslog collector. With the syslog agent, logs are sent to our cloud infrastructure for analysis & subsequent storage.
simplifying compliance
& reporting for cloud applications
A strong security strategy to prevent attacks, detect potential breaches, and protect customer data by identifying suspicious logins, including fraudulent activity and geo-impossible logins. Deeper insights into the health and performance of your cloud and on-premise infrastructure within a single platform.

Services hosted in all AWS FedRAMP Levels
Services can be hosted in GovCloud/GCC High
Optional long-term storage of security logs in AWS FedRAMP or GovCloud environment to support compliance requirements.
Regulatory Compliance
SOCSoter helps organizations meet IT compliance regulations by monitoring, managing, and providing necessary data for reports. Our centralized reporting intelligence allows customizable audit-ready reports that help you meet major regulations.
Third-Party Risks
Third-party security monitoring can highlight undetected vulnerabilities in a server-less ecosystem. Efficient monitoring & distributed tracing reveals attack flows & their potential impact, so you always know how to respond.

modernize your operations & view the threats that matter most
Schedule your demo today and explore how Cloud SaaS Security Monitoring can enhance your business security