cybersecurity COMPLIANCe
Gap Assessments | Risk Assessments | POAM Development | Compliance Coaching
SOCSoter delivers cybersecurity compliance with a comprehensive and approachable solution, simplifying even the most complex regulatory requirements. Our certified experts partner with businesses to tailor strategies that align with their size, operations, and compliance needs, ensuring they achieve and maintain industry regulation standards with confidence.
Most cybersecurity compliance regulations require the same thing, but they use different words to convey the message. The difficulty most small organizations encounter is translating controls into how their business operates, & finding or configuring the technology to satisfy the requirements.
Solidify Your Strategy
Detail Requirement Alignment
Designed by experts. built for the unexpected.
compliance Made Simple!
navigating your regulation needs

EVALUATE / ASSESS

ANALYZE & UPDATE

GUIDE & DEVELOP

CREATE / REMEDIATE
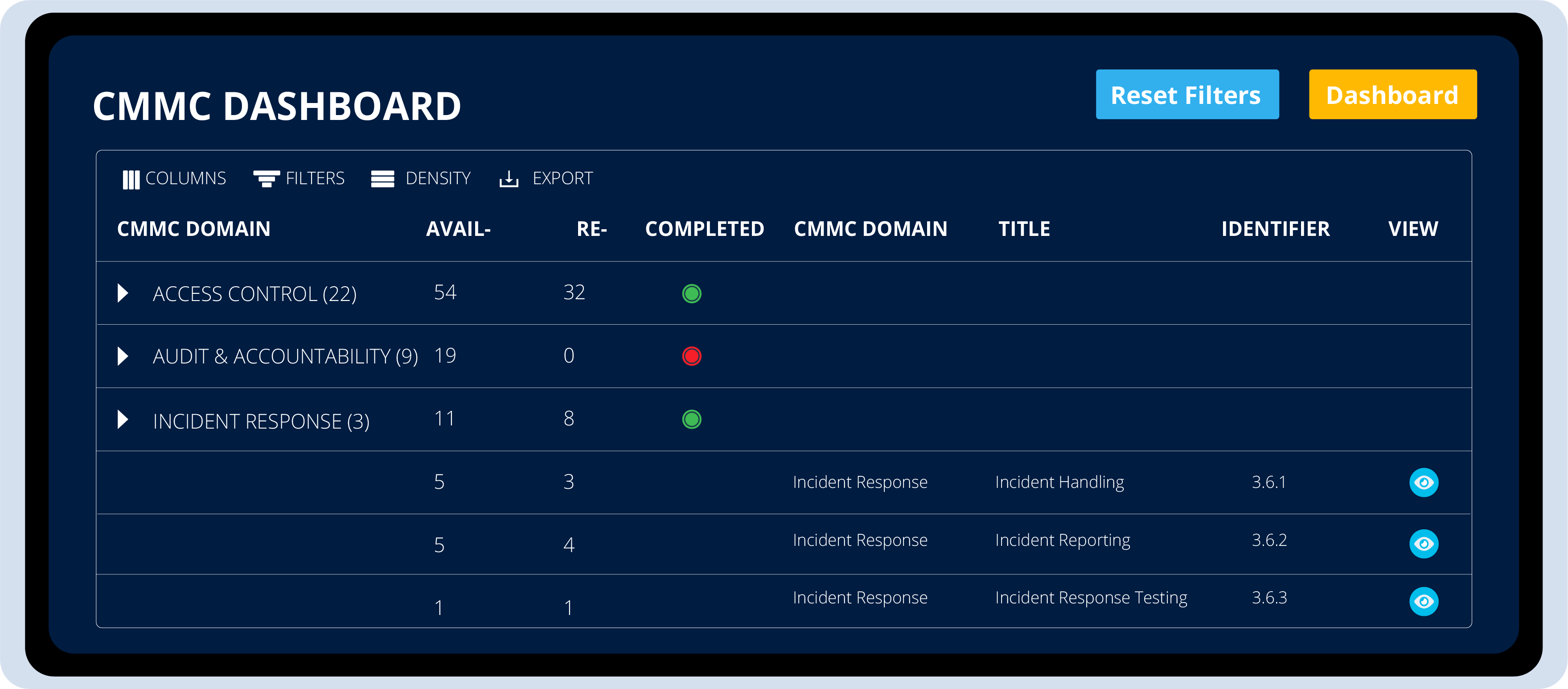
25% Technology
24/7 US-Based SOC SIEM, Vulnerability & log storage
SOCSoter’s SOC-SIEM, Vulnerability and secure log storage delivers essential security services and comprehensive oversight, empowering organizations to proactively manage threats and maintain cybersecurity compliance.
75% documentation
Policy Creation & Service Documentation
The foundation of any cybersecurity compliance program, in terms of organization & management, is to document procedures & technology implementation to satisfy the regulatory requirements.
policy-based Strategy,
Guidance by Insight
meet or exceed various cybersecurity compliance obligations, regulatory, & supply chain demands








The SOCSoter platform offers a comprehensive services portfolio specifically crafted to mitigate rising cyber threats, enhance regulatory compliance, and align with stringent regulatory standards.
Evaluate & Assess
Comprehensive Coverage
Understanding the intricate layers of your digital infrastructure is paramount.
SOCSoter identifies gaps in your security measures and guides you in meeting cybersecurity compliance standards. By aligning your policies and technologies with compliance frameworks, we help you understand each requirement and implement clear, well-documented roles, access, and procedures tailored to your business needs.
Compliance Assessments
Tailoring complex regulatory requirements to fit the needs of small businesses and their MSPs. We break down enterprise-level standards into actionable steps that make sense for your business, ensuring roles, access, and documentation are clear, well-managed, and aligned with your unique operational needs.
Bridging the Compliance Gap
Step-by-Step Risk Alignment! Break down each control, to determine regulation readiness & identify any gaps. We clarify which controls your business needs to implement, & evaluate how well they align with your current operations.
translate regulations
Translating complex regulatory language into clear, actionable steps, ensuring that navigating cybersecurity compliance requirements is accessible & comprehensible for anyone.
We do this by providing expert guidance, conducting gap assessments, & creating Plan of Action and Milestones (PoAM)
Guide & Develop
assess Processes, Verify Functionality
Review current policies, technologies, roles and responsibilities and work with the MSP and customer on how to best satisfy the controls with existing resources and culture. Working together to find the best solutions.
Review Documentation
Is your IT & security deployment fully documented & aligned with cybersecurity compliance standards?

Identify key roles and responsibilities and determine who would be responsible for what and if any changes need to be made.

Assess technologies currently being used and determine if the technology is deployed and configured correctly and decide if any new technologies need to be introduced.

Educate key personnel on their duties and teach them how to execute them.
recommend Remediation
The foundation of any compliance program!
Clear guidance on meeting each cybersecurity compliance control, identifying gaps in your processes and offering specific, approved actions for remediation.
By asking the critical questions, we uncover what’s missing & guide you on closing those gaps effectively & securely —
Where is your protected information stored?
How do you transmit it?
What level of encryption does the regulation require?
Who has access to your protected information?
Do you know how to configure your systems to satisfy the controls of the compliance framework?
Create & remediate
Oversee Deliverables & Objectives
Manage deliverables, uphold key objectives, and clarify responsibilities, all while driving the compliance requirements across the company. This is done by helping create a culture that promotes ethics, transparency, and accountability.
Keep deliverables on track
Do you understand what your security reports are telling you?
assist the organization to complete poam items
Assist the organization to prioritize certain action items to best satisfy customer & compliance frameworks.
develop robust policies & procedures
Create policies & procedures by ensuring they accurately reflect what the organization is doing.
implement effective internal control
Create documentation to ensure the organization can effectively follow its policies & procedures.
review reports for audit
Ensure the organization’s technology is deployed correctly & performing in accordance to the organization’s polices.
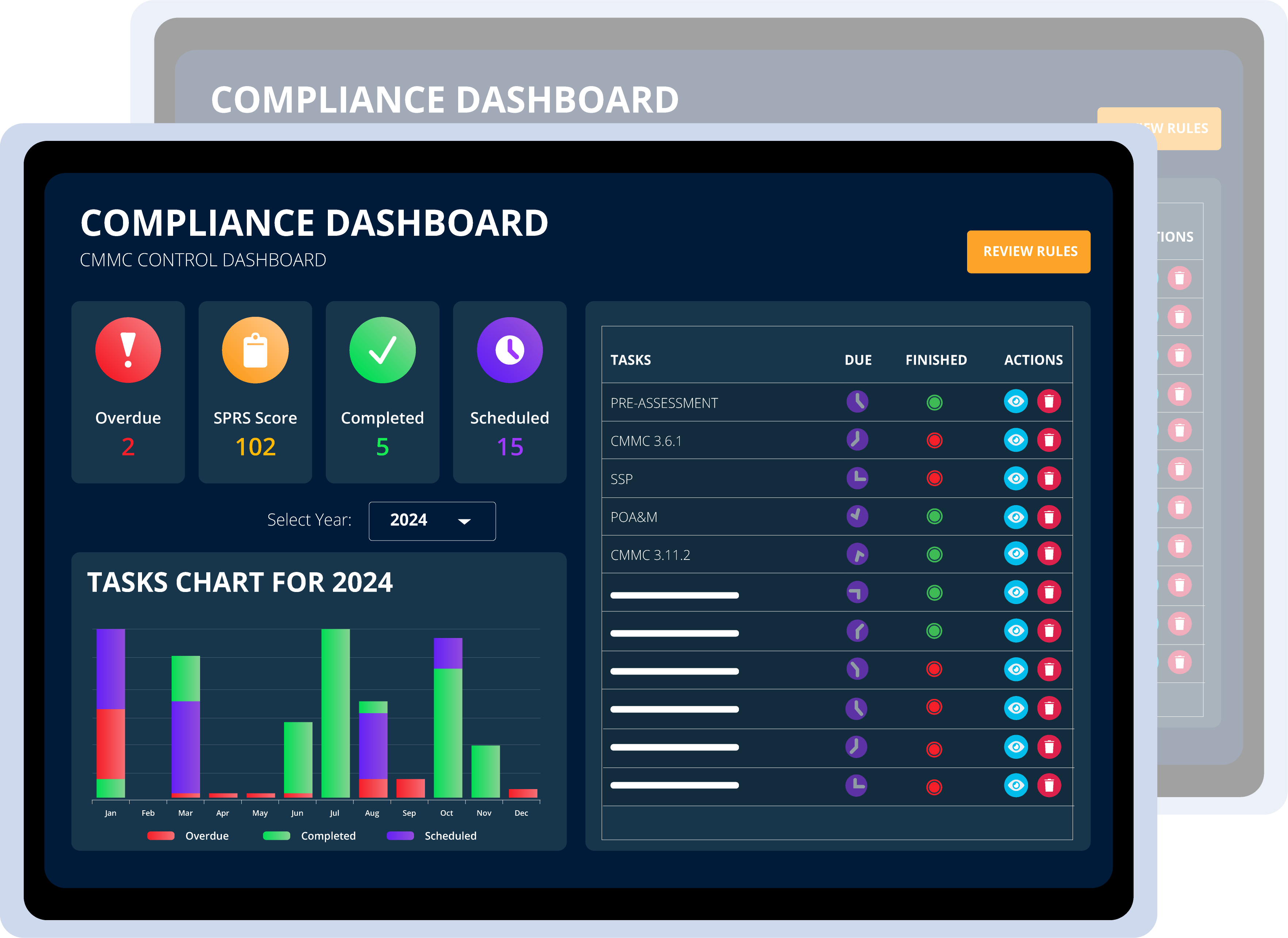
Continuous exposure visibility
Maintaining asset compliance is crucial to avoid breaches, penalties, and enhance security. Continuous assessment offers real-time visibility and insights to achieve and sustain compliance.
Real-time visibility
By constantly monitoring for vulnerabilities, organizations can identify compliance issues as soon as they arise, preventing potential breaches or penalties.
Audit Evidence
Regular assessments demonstrate cybersecurity compliance to auditors, reducing audit failure risks. Often identifying security vulnerabilities & improving overall system security.
risk mitigation
Continuous assessment helps to identify vulnerabilities & misconfigurations before they can be exploited, reducing the risk of non-compliance.
Streamline compliance From POAM Prioritization to Effective Internal Controls & Audits
analyze & update
Supporting Every Step of Your Journey
When the time comes to take action, we don’t simply leave you to figure things out on your own; we’re here to support you every step of the way!
Comprehensive Support
continuously Optimizing Your Compliance Framework
1
Identify key roles & responsibilities to determine who 0would be responsible if any changes need to be made.
2
Assess technologies currently being used & determine if the technology is deployed & configured correctly.
3
Educate key personnel on their duties & teach them how to execute them.
Configuration Compliance
Different organizations have different regulatory requirements. Which can be hard to track!
Take the guesswork out of your compliance requirements with our innovative Security Content Automation Platform (SCAP)-compliant capability.
This feature provides a fully customizable compliance and security enhancement program. Automate security content scanning to assess your systems against established best practices like DISA STIGS & CIS Benchmarks.
Security Content Automation & Discovery
Utilizing SCAP technology, our system automates configuration discovery and policy compliance checks, eliminating the need for manual audits and saving time and resources. This evaluation assesses your system’s configuration and policy compliance to measure adherence levels.