vulnerability management for strategic risk mitigation
Effective vulnerability management for risk mitigation means moving from the activity of scanning for vulnerabilities to managing them. Gain actionable insights to implement effective measures that mitigate or eliminate associated risks and move the needle on protecting what matters. True management of exposures goes beyond scanning.
Endpoint | Network | Cloud | Vulnerability | Compliance

Built for visibility. Designed to be proactive.
Don’t just identify vulnerabilities
understand & neutralize them

EXPOSURE MONITORING

VULNERABILITY MANAGEMENT

VMDR
managing Risk beyond scanning
to stay ahead of evolving threat
Streamlined Prioritization
Relying on just scan results creates complexity, instead use asset management to identify key targets and prioritize exposed systems first.
Beyond Traditional Assets
We don’t stop at traditional assets. SOCSoter scans your entire network environment, including IoT devices, for potential weaknesses. This holistic view provides a complete picture of your security posture.
integrated threat intelligence
Enhancing reporting capabilities by offering real-time vulnerability metrics that prioritize threats based on severity and exploitability. Actionable data + threat intelligence, means you can concentrate on vulnerabilities most likely to be targeted by attackers
risk-based Prioritization,
Powered by continuous monitoring
Stop scanning, start managing
vulnerability management
detection & response (VMDR)
With effective vulnerability management for risk mitigation, you can achieve comprehensive vulnerability coverage with real-time visibility into your organizations security posture. Identify risks proactively, understand the exposures, receive actionable insights, & eliminate blind spots.
Most organizations stop at scanning

detect vulnerabilities
Identify potential weak points in your system.
ASSET DISCOVERY
ATTACK SURFACE
THREAT INTELLIGENCE

The + Factor goes beyond the initial stage to manage risk

assess exposures
Understand the potential impact of vulnerability
out-of-date software
misconfiguration
asset compliance


prioritize severity
Some vulnerabilities need immediate attention
nv database publishing
cvss risk scoring
real time insight


manage remediation
Implement solutions to address each vulnerability
custom escalations
custom alerts
detailed reports

security operations center evaluation
24/7 Expert analysts | False Positives | Risk Acceptance | Rule Creation | Comprehensive Documentation
Effective vulnerability management for risk mitigation
While scanning for vulnerabilities keeps you informed, managing exposures provides the insight necessary to prioritize the weaknesses that pose the greatest risk to your organization.
The Power of a Layered Approach
comprehensive coverage
going Beyond the Scans
Gain a unified view of your organization’s vulnerability landscape, streamlining tracking & management to prioritize risks effectively.
Access key metrics and insights all in one place to bolster your security strategy and enhance risk mitigation.
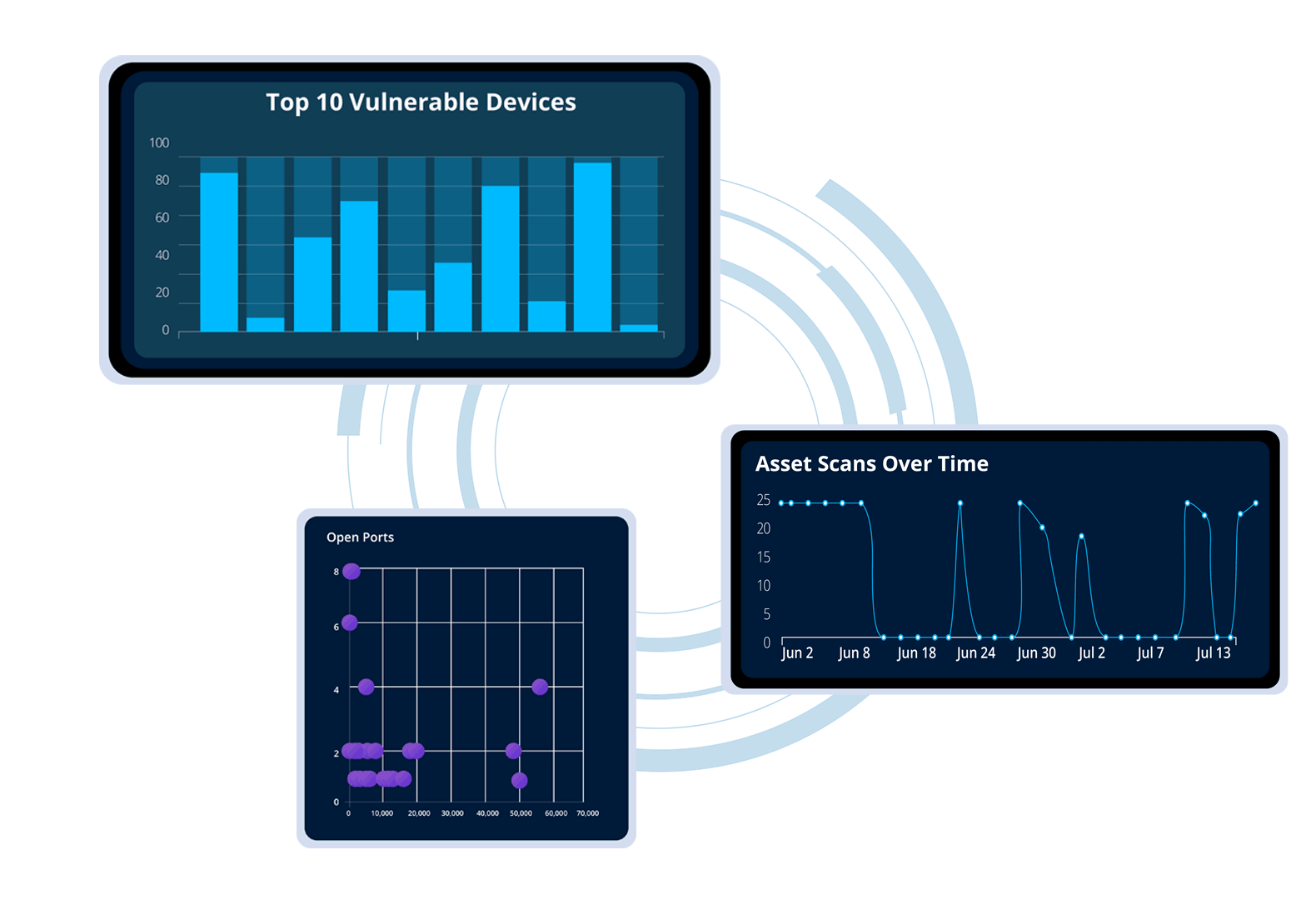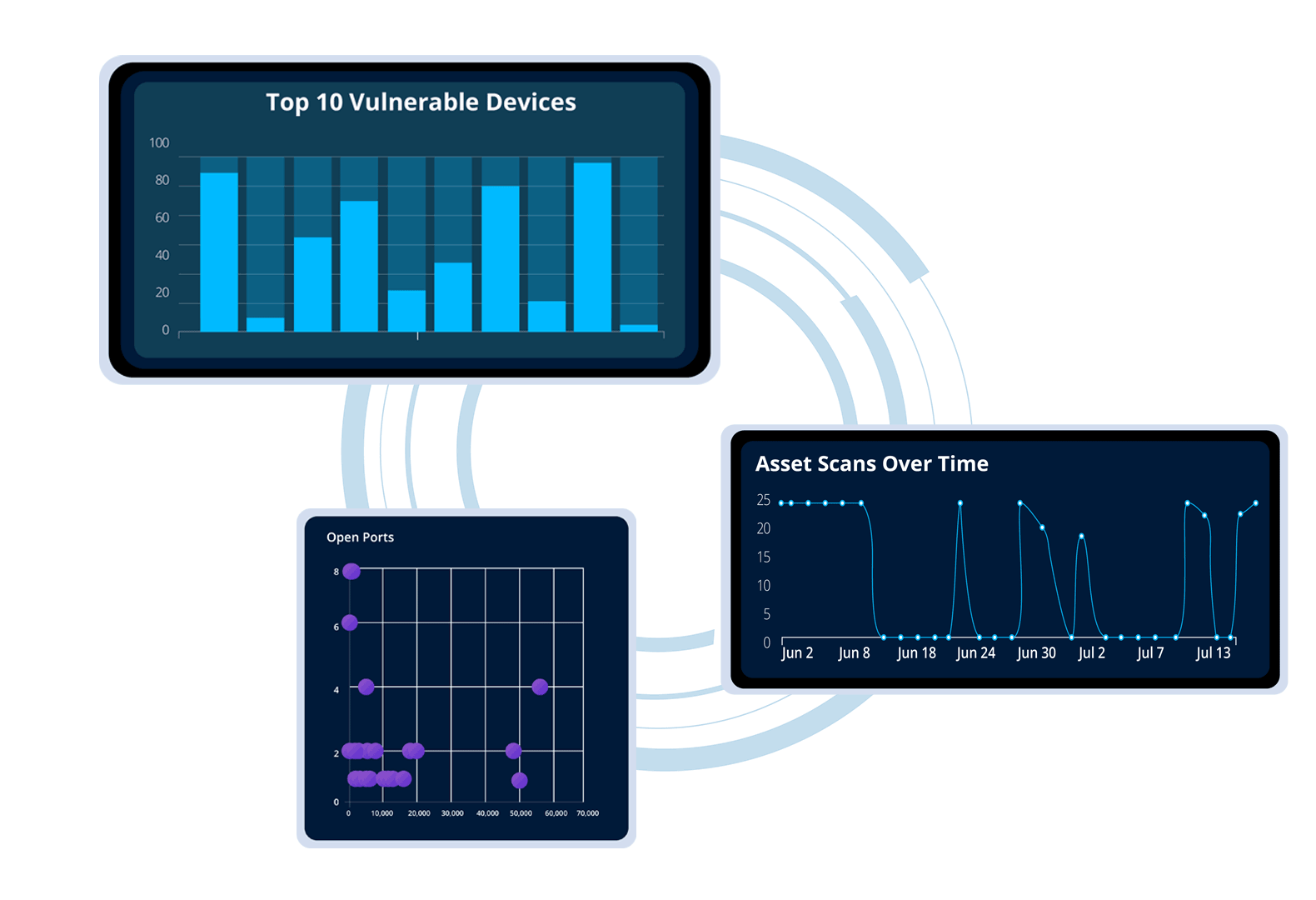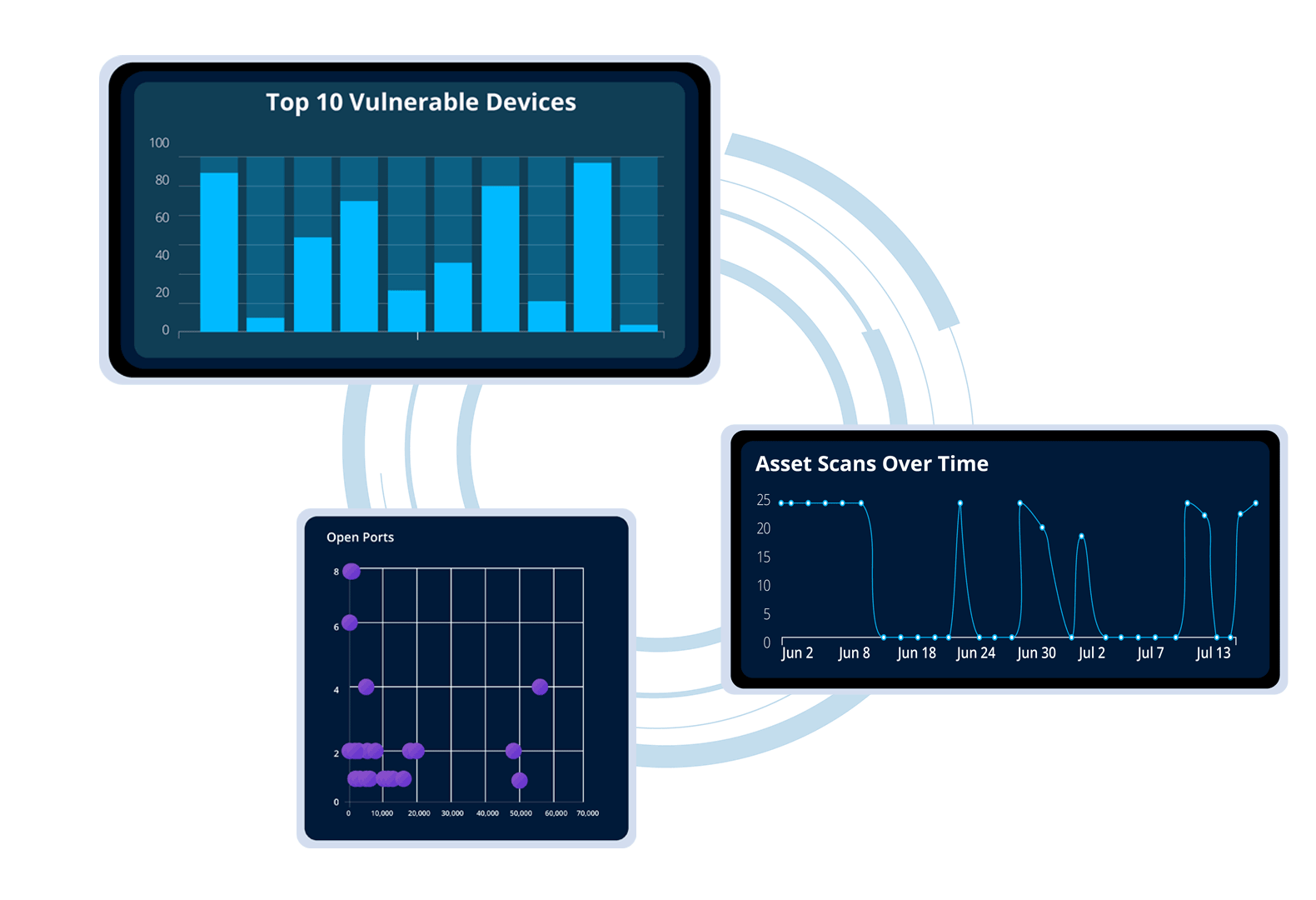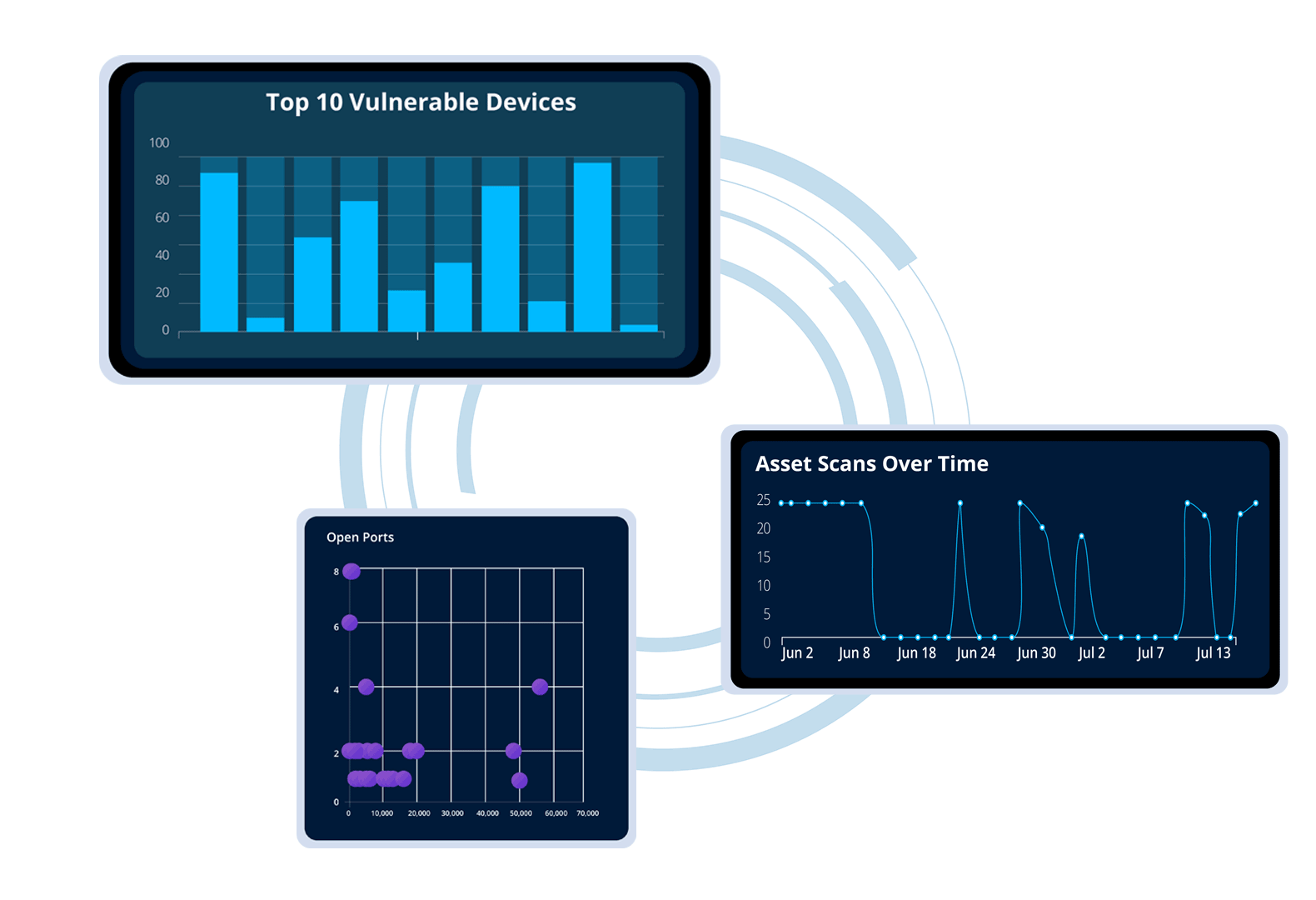
Monitor & manage your IT infrastructure as a whole, no matter where individual devices are located.
continuous threat monitoring
By continuously monitoring your network and systems, we can identify vulnerabilities and potential attack exposure as they occur. Allowing organizations to respond to vulnerabilities quickly, reducing the risk of breaches and minimizing impact.
Leveraging Intelligence
Effective vulnerability management for risk mitigation
Stay Ahead of the Curve,
by leveraging both human and machine intelligence to uncover global threats and gain real-time insights. Securing your foundation involves harnessing continuous threat intelligence to accurately assess risks and understand your exposure, enabling effective mitigation and protection of your infrastructure.
It’s not just about reacting to threats as they arise—it’s about anticipating them, understanding them, and taking decisive action to prevent them.
Proactive defense
By integrating continuous scanning, organizations can identify & address vulnerabilities closer to discover instead of waiting for the monthly report.

enhanced visibility
Always On offers fast insights into the threat landscape, aiding organizations in understanding potential exposure ripe for attacks.
Automation
Leveraging automated vulnerability scanning enables the management of vulnerabilities instead of waisting time on managing scans.
from reactive to proactive
Reduce Risk, Enhance Resilience
Continuous vulnerability management
Detecting malicious activity and insider threats, while staying updated on important findings.
Visibility into an organizations infrastructure consistently evaluates their security framework to ensure adherence to internal information security protocols and external compliance standards.
Assess real-time Exposures
Evaluate the importance of the assets that could be compromised.
With ongoing evaluation of your systems, vulnerabilities, & configurations, automated scans & reviews ensure that your security measures are up-to-date & resilient.
Continuous assessment maintains effective vulnerability management for risk mitigation by proactively maintaining & enhancing your security posture, preventing vulnerabilities from ever becoming threats.
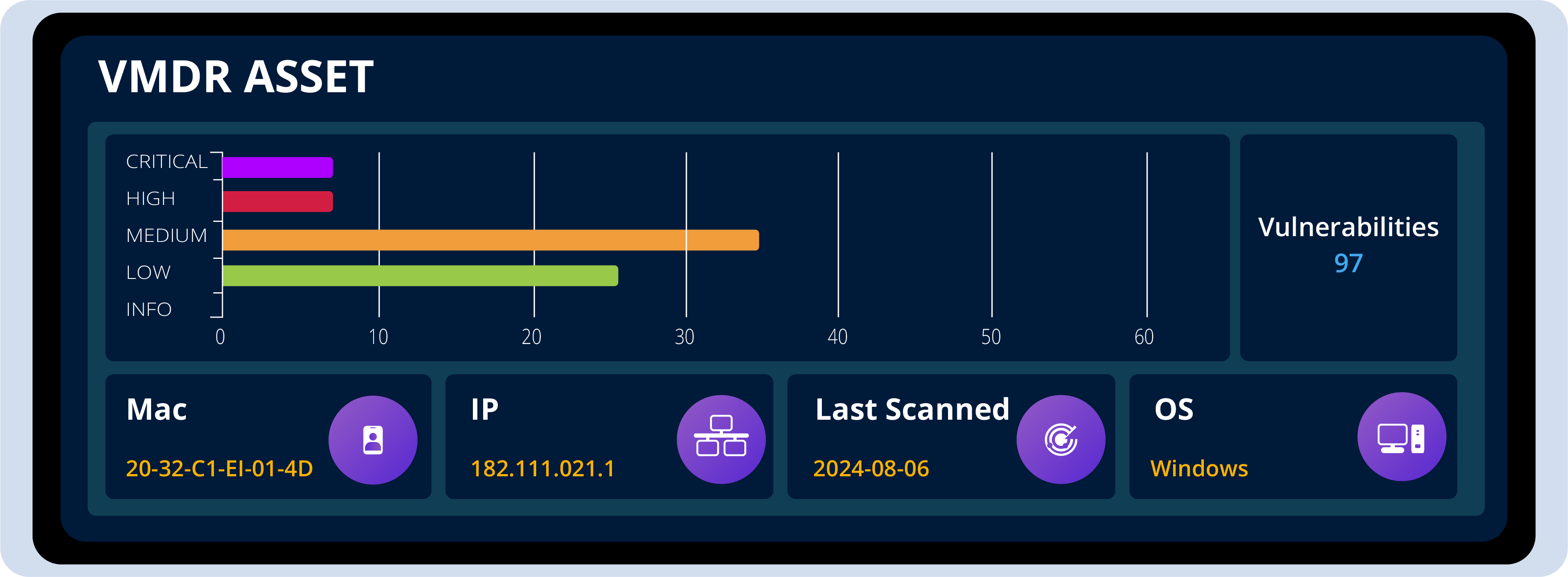
By examining a single asset in detail, you can uncover & address multiple vulnerabilities associated with it, potentially resolving several issues at once.
When you can target deeper insight it becomes easier to reduce the overall workload & enhance your security efficiency by focusing on critical assets.
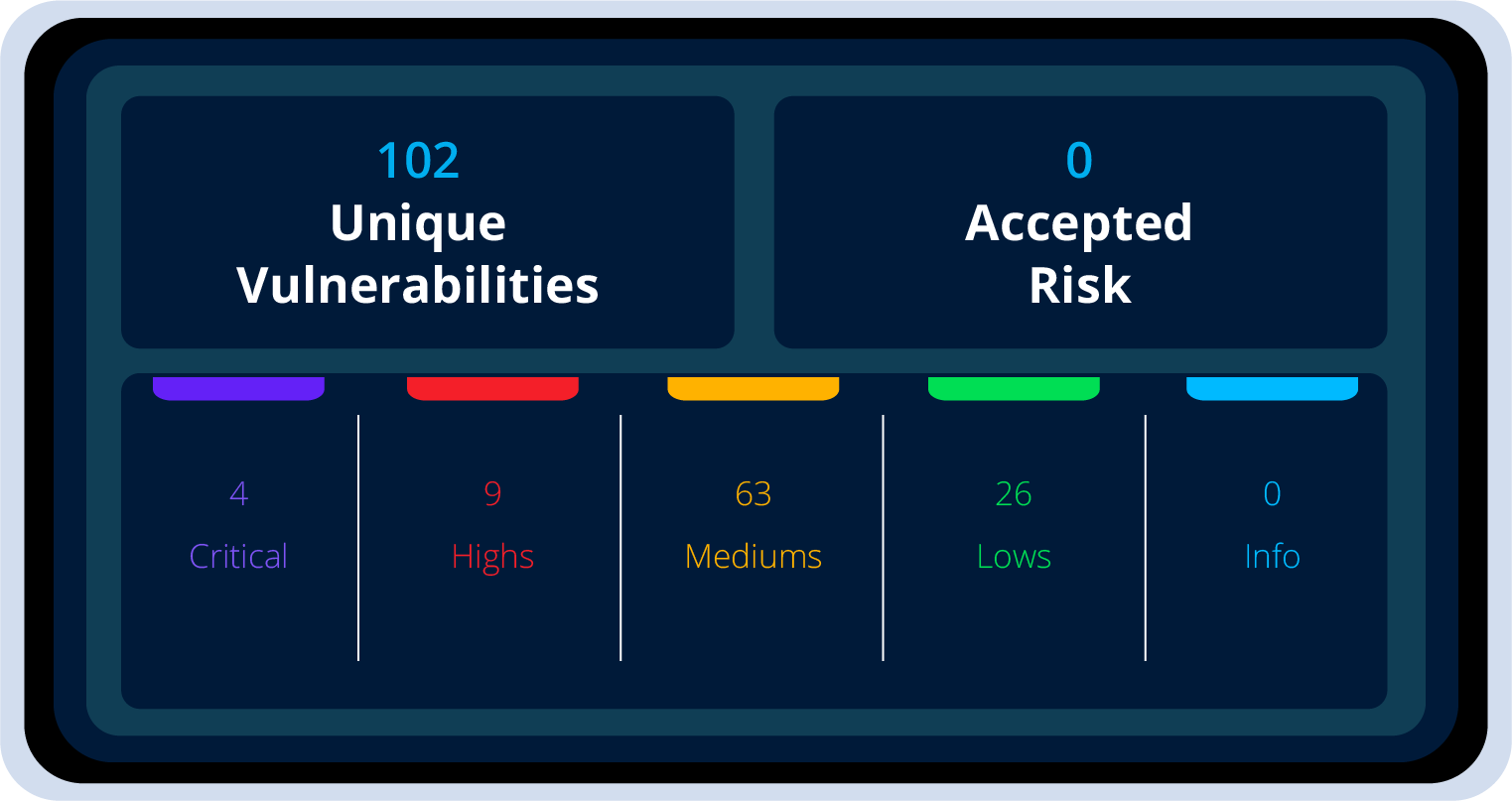
Understand Your data to Prioritize Action
To prioritize effectively, you must understand the source & potential impact on your system.
This requires an understanding of your system’s weaknesses & the threats they pose. Effective vulnerability management for risk mitigation means knowing the value of your assets, reducing your attack surface, & evaluating the likelihood of exploitation with current threat intelligence.
Not all vulnerabilities are created equal. Some exposures pose a greater risk to your organization than others.
When you understand the exposures, you can prioritize remediation based on their risk.
FOCUSED REMEDIATION management
A targeted approach with deeper insight reduces overall workload & enhances your security efficiency by focusing on critical assets.
A centralized view allows you to prioritize all vulnerabilities by severity, streamlining your efforts. Effective remediation is crucial to protect your organization’s assets while maintaining a strong security posture. Critical exposures are visible in ONE centralized hub for prompt, informed decision-making.
Results that prove effective vulnerability management for risk mitigation are constantly uploaded to the portal, allowing users to evaluate vulnerabilities, set priorities & generate reports that help drive remediation.
YOU MAY NOT SEE A LOT OF DATA…
But that’s the point!
With effective management of your infrastructure, you can leverage custom rule creation, along with capabilities like escalations, risk acceptance, asset tagging, and auto-generated tickets.
Minimize unnecessary noise and streamline the remediation process by customizing the system to meet your specific needs.
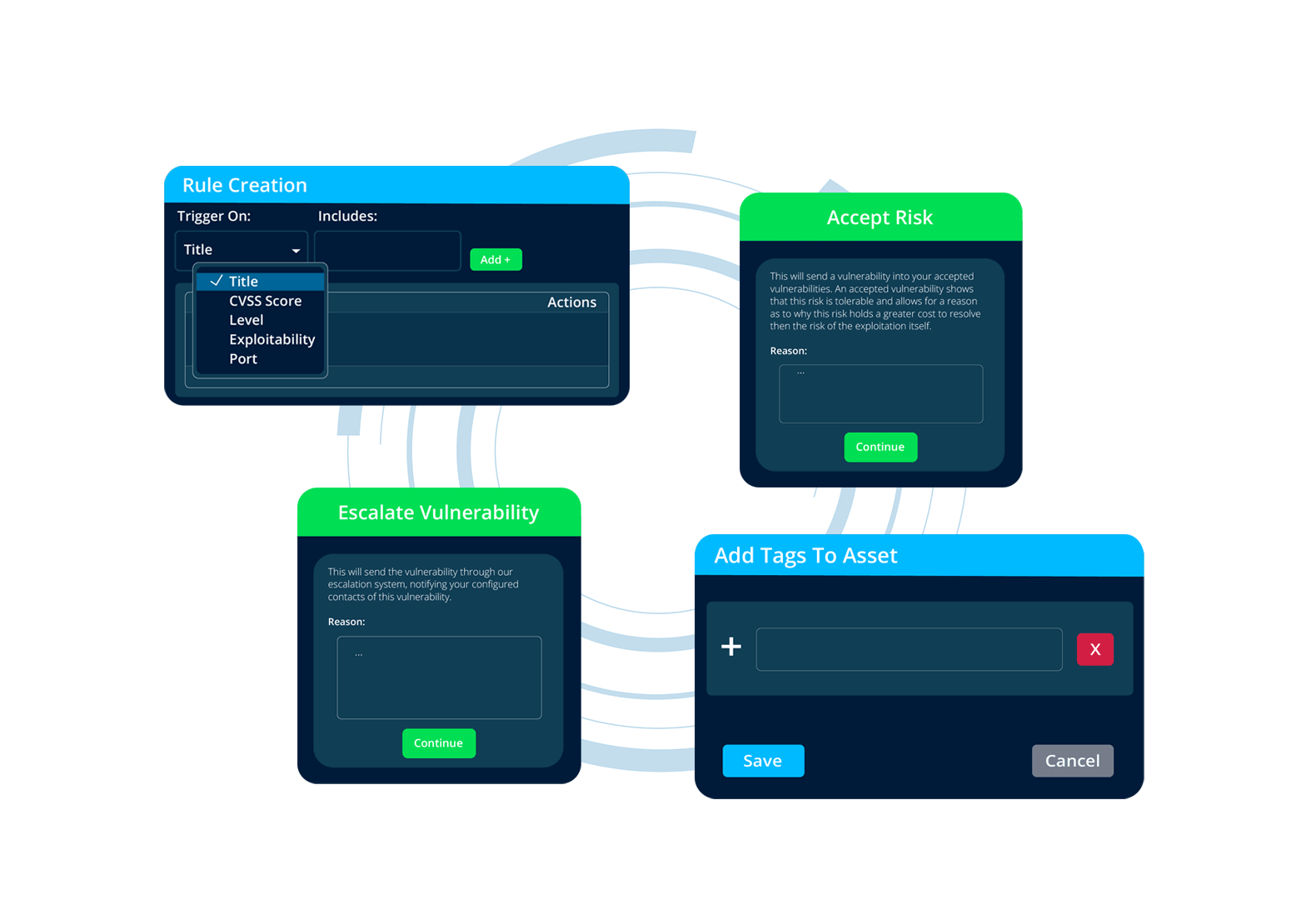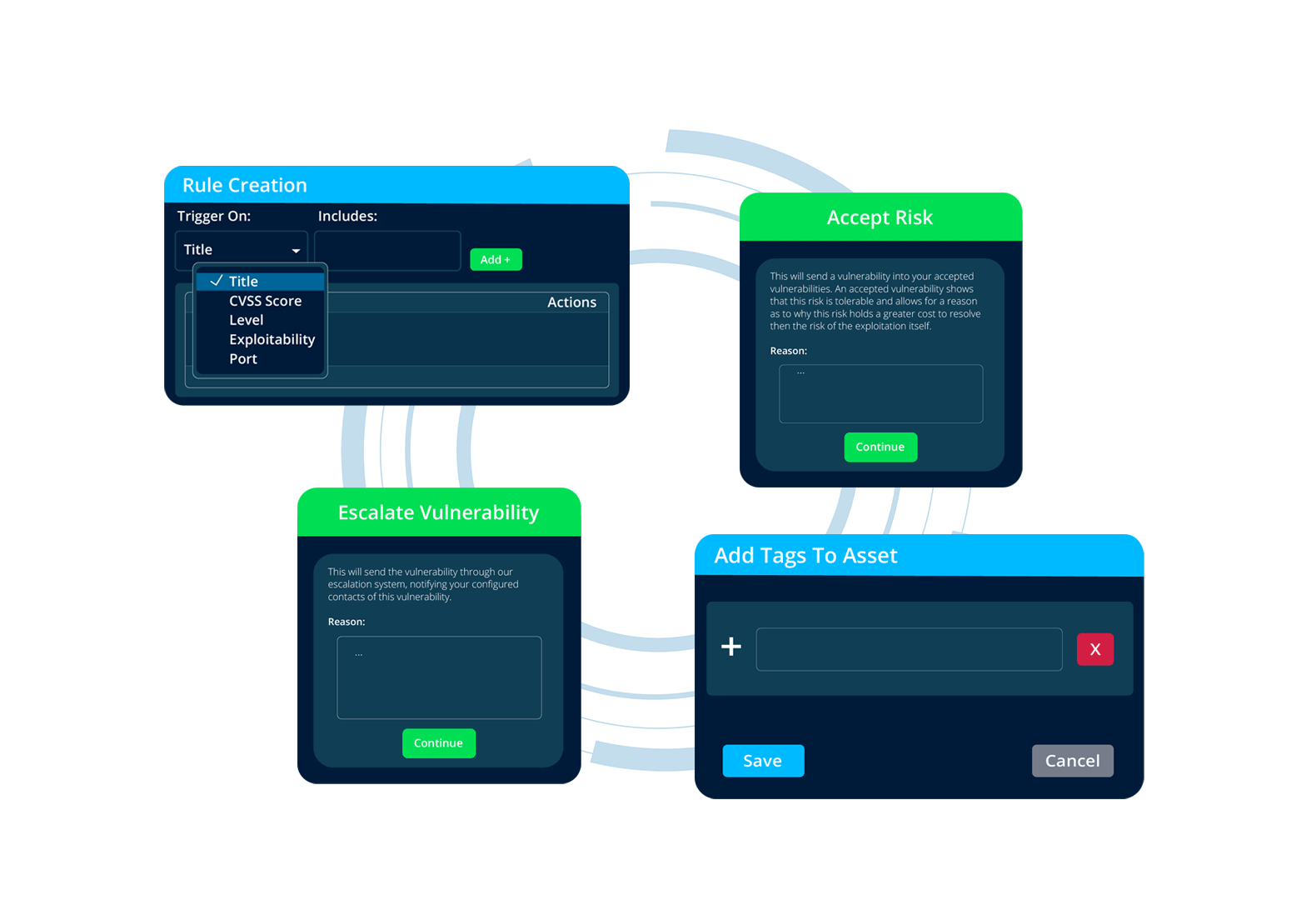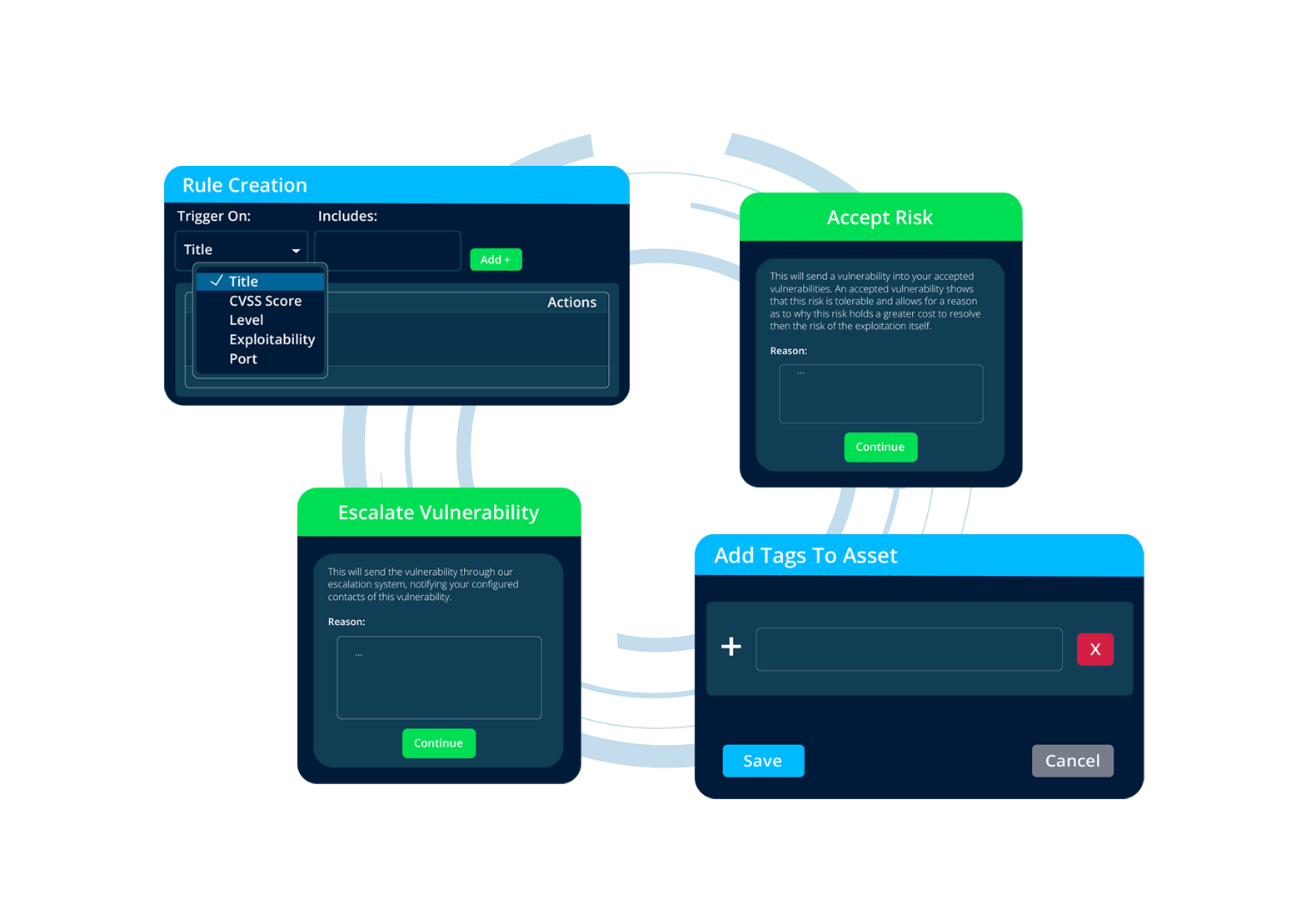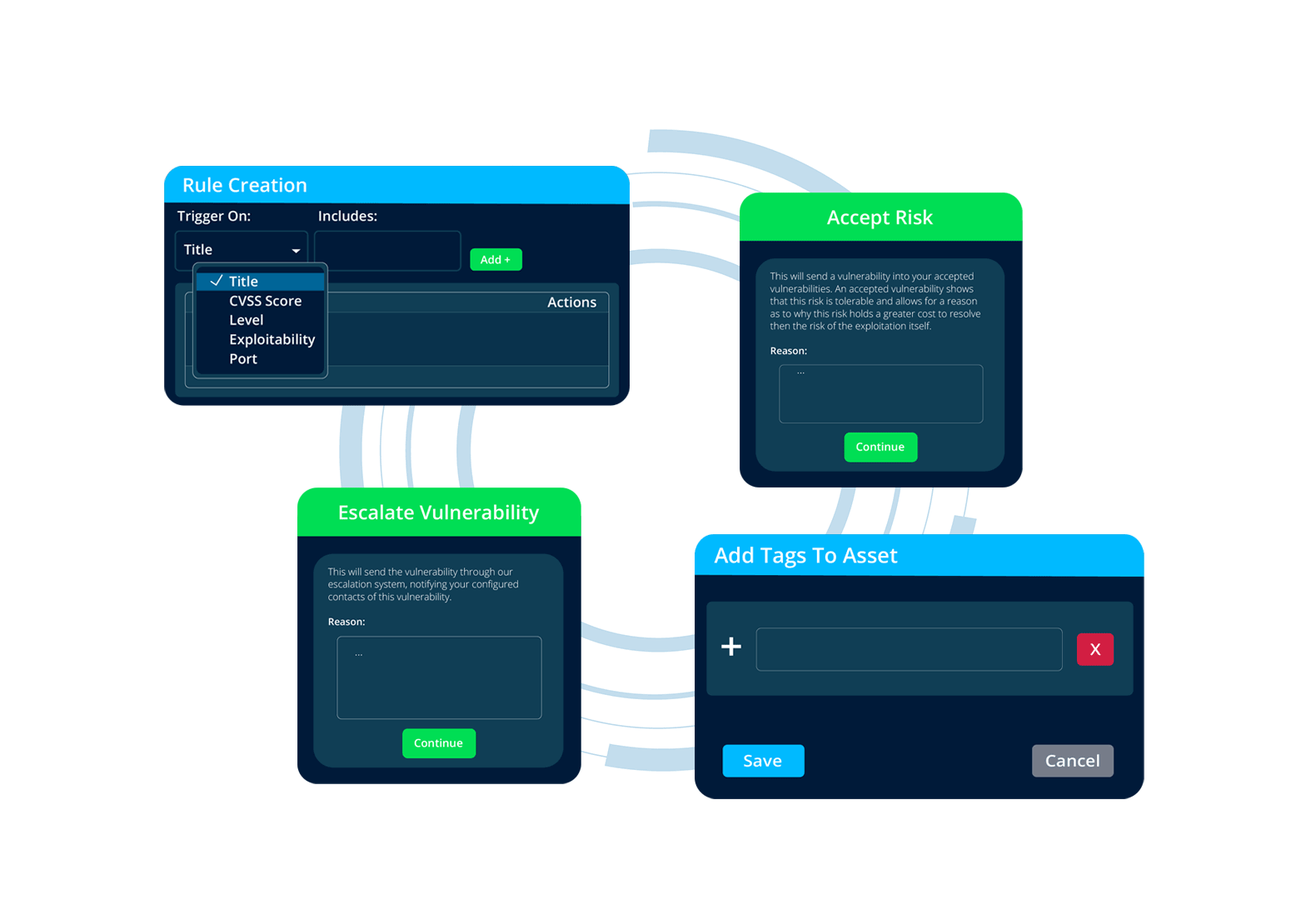
Focus on Risk, Not Just Detection
prioritize what actually Matters
Effectively managing vulnerabilities requires more than just identifying them—it demands prioritizing them based on their severity and exploitability and exposure.

prioritize fixes, updates, & patches like software updates & configuration changes
Monitor & Verify Remediation After implementing fixes to potential vulnerabilities
confirm resolved issues did not introduce new vulnerabilities
Keep detailed records of all remediation issues addressed, actions taken, & challenges encountered
Provide regular progress reports & update security documentation to reflect the current state
continuously review your remediation processes & strategies to identify areas for improvement
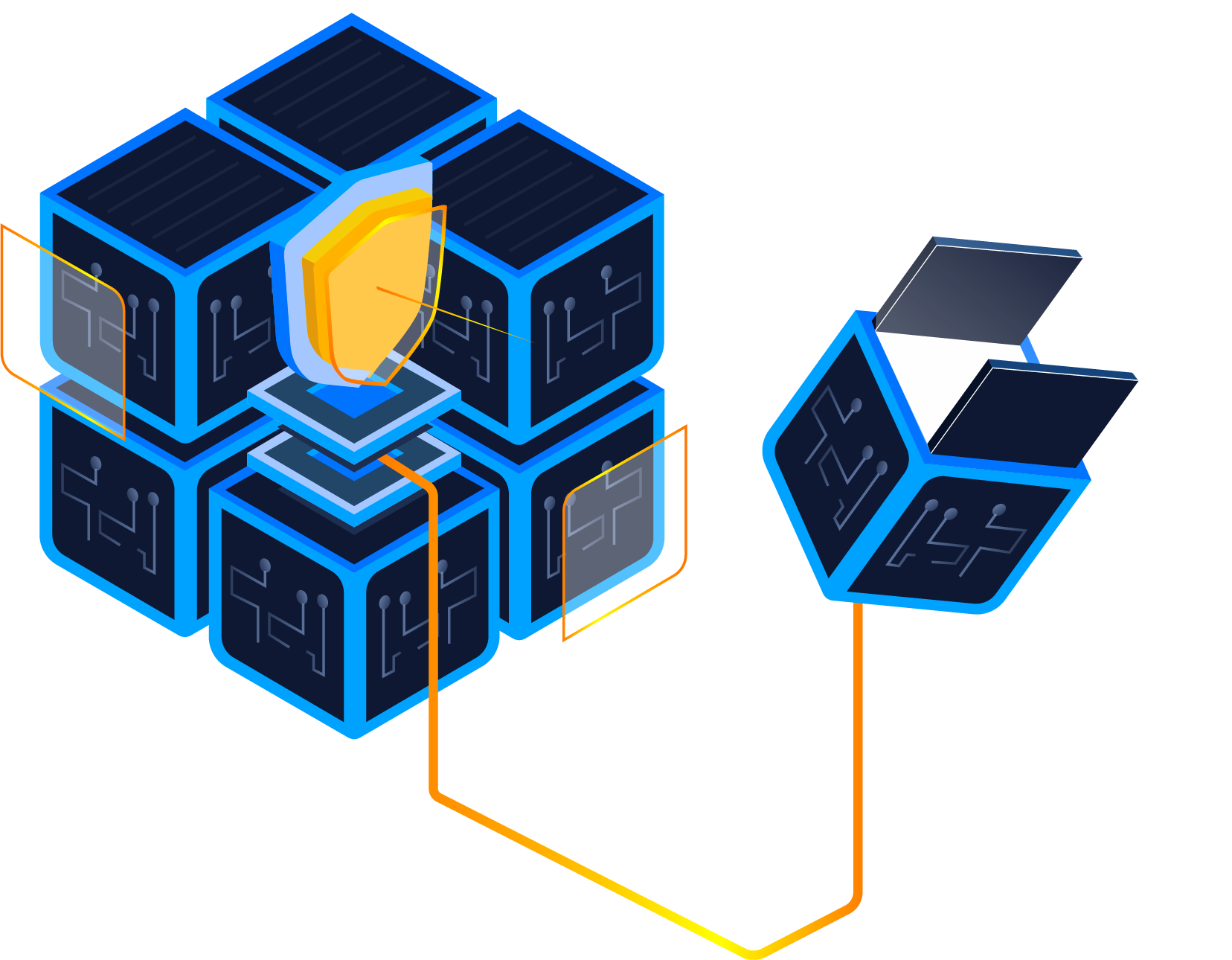
maintaining Asset Compliance
Continuous exposure visibility
Maintaining asset compliance is essential for avoiding breaches, penalties, and ensuring robust security. Continuous assessment plays a crucial role in achieving and sustaining compliance. By providing real-time visibility and insights into your asset environment, you gain effective vulnerability management for risk mitigation.
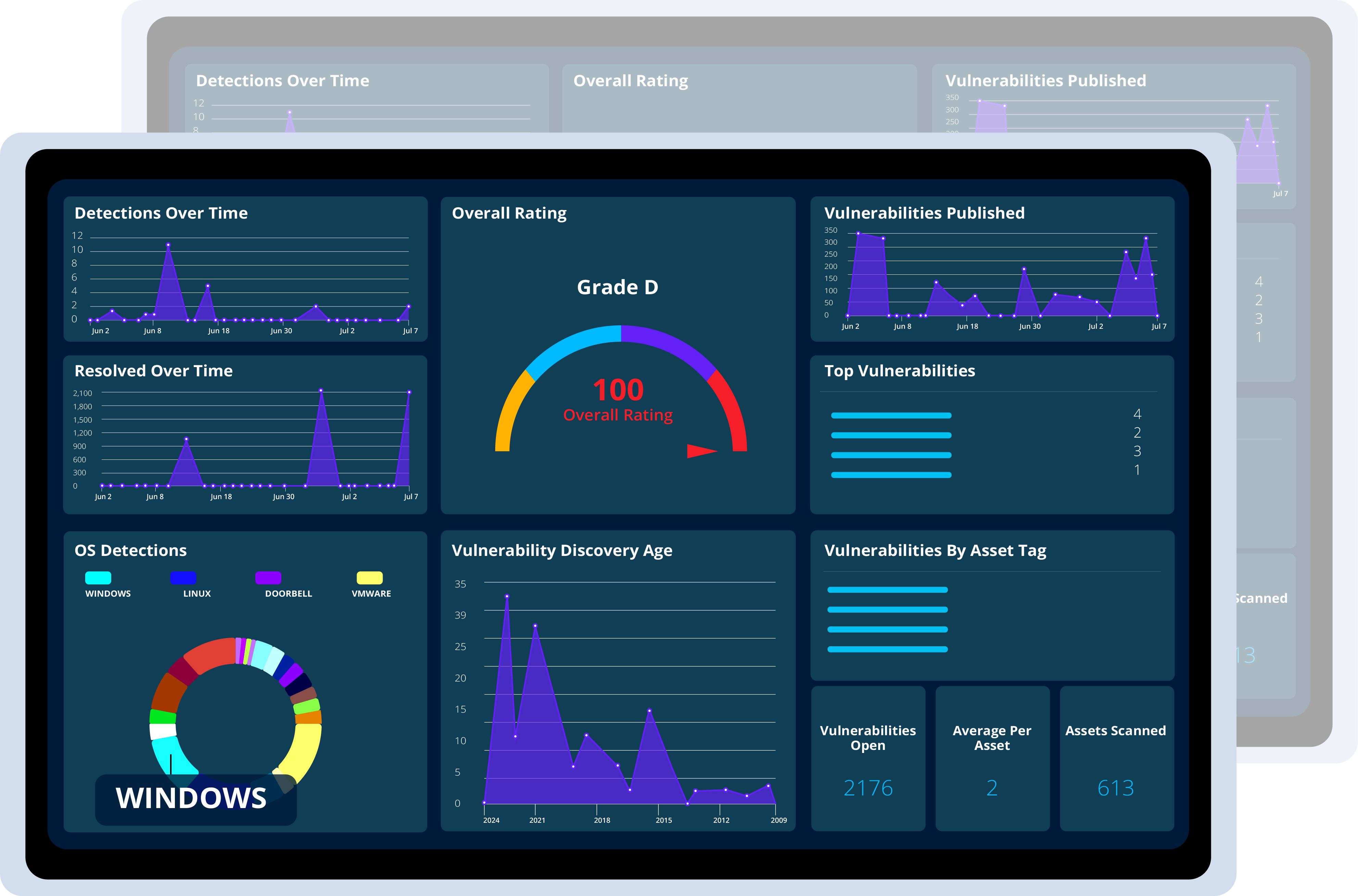
Consolidated view of detections over 30 days
Visual of monthly vulnerabilities that were solved
Summary of vulnerability age from when it was first detected
View overall organizational rating based on custom scoring
Total operating systems detected within the organization
VMS information based on newly published and top vulnerabilities
real-time visibility
By constantly monitoring assets, organizations can identify compliance issues as soon as they arise, preventing potential breaches or penalties.
audit evidence
Regular assessments demonstrate compliance to auditors, reducing audit fail risks. Identifying security vulnerabilities & improving overall system security.

risk mitigation
Continuous assessment helps to identify vulnerabilities & misconfigurations before they can be exploited, reducing the risk of non-compliance.
incident response
By having a clear understanding of assets & their compliance status, organizations can respond more quickly to security incidents.

look beyond cvss scores
Consider factors such as age, exploitability, and impact. Our system integrates automatic data updates from the National Vulnerability Database (NVD) to keep vulnerability data current and aligned with industry standards.
If you’re looking to uncover new and previously unknown threats beyond what vulnerability scans and CVSS scores reveal, click here to learn more about our Penetration Testing Packages. This comprehensive approach will help you effectively address both recognized and emerging vulnerabilities.

It’s not just about identifying vulnerabilities
it’s about understanding them
SCANS OVER
10M
WEB PAGES DAILY FOR DATA GATHERING
ANALYZES
1.5M
MESSAGES DAILY FOR THREATS VIA SPAM/PHISHING TRAPS
COLLECTS DATA FROM
>330M
ENDPOINTS GLOBALLY ON A REGULAR BASIS
DEPLOY YOUR WAY!
Both options work the exact same way. These options are offered to accommodate for different business conditions where one or the other may not fit.
Support for Windows, macOS, & Linux based on your organization’s needs.
different organizations
HAVE DIFFERENT DEPLOYMENT NEEDS
There’s no one-size-fits-all solution. That’s why we offer flexible deployment options tailored to your unique needs. Our solutions adapt to your business conditions, ensuring not just a service, but the right service for you.

ALWAYS ON
CONTINUOUS MONITORING
NETWORK-BASED | LOW IMPACT UTILIZATION
MOST FRAMEWORKS ARE TRENDING TOWARD THIS OPTION
More Efficient for Teams
Reduces Work Load
Around the Clock Network Updates
VIRTUAL APPLIANCE OR ON-PREMISE HARDWARE APPLIANCE
- Lightweight enough to run 24/7/365 & deep enough to discover all vulnerabilities.
- Many compliance requirements require correlation of vulnerabilities to CVSS scoring.
- Vulnerabilities added to data feed automatically upon publication without requiring manual updates.

ENDPOINT
REAL-TIME DEVICE SCANS
NO NETWORK, NO PROBLEM!
BEST FOR REMOTE & HYBRID ENVIRONMENTS
Ongoing Daily Scans
Off-Network Monitoring
Software Change Updates
ENDPOINT AGENTS DISCOVER SYSTEM FLAWS AUTOMATICALLY
- EDR technology for ongoing scanning, real-time monitoring, & visibility into the security status of endpoints, even when they aren’t connected to the network.
- Data securely pushed to the Vulnerability Management dashboard for evaluation that can provide actionable insight, enabling quick prioritization.

ONE TIME
QUARTERLY SCANNING
NETWORK-BASED | REMOTE VPN
FOR circumstantial SPOT-CHECKING AS NEEDED
Compliance Requirements
Client Prospecting
INTERNAL REMOTE SCANS TO FIND & PRIORITIZE ENTRY POINTS
- One-time, quarterly, or custom scheduled scans available.
- Often required for audits & compliance requests to show current network security posture.
- Useful resource to provide prospects a security report of their exposures to align security services needed.